by Michael Cropper | Nov 11, 2016 | Client Friendly, Security |
There has been a fix come out which patches a sever vulnerability in the OpenSSL technology in use on many Linux web servers. Be sure to update your web servers to prevent this vulnerability being exploited. For a full technical write up on the vulnerability, head over to Threat Post who have covered the topic in great detail.
The vulnerability was first identified by an information security engineer at Google.
What do you need to do?
Install the latest OpenSSL patches available on your Linux web server. Speak to your web hosting company to get this updated. Clients hosting with us, our web servers have been patched as soon as the vulnerability patch was made public.
We strongly recommend running a manual server check if an automatic patch isn’t available to you. If you have any questions regarding the vulnerability or your solution please contact me and I can talk you through the solution.

by Michael Cropper | Nov 11, 2016 | Client Friendly, Security |
You may have seen the news about a Linux vulnerability branded ‘Dirty COW’, which affects many Linux servers. An overview of the vulnerability is below and what you need to do.
What is Dirty COW?
Dirty COW is a new Linux vulnerability referred to technically as CVE-2016-5195. The name came from the fact that it exploits a mechanism called ‘copy-on-write’ and is known as a privilege escalation bug. This means that if attackers manage to get a foot inside your system they can then use Dirty COW to take total control, so it’s crucial to protect yourself. The bug has only recently came to fruition but has been around for nine years – which means it’s likely that many Linux servers have been affected.
What do you need to do?
Install the latest Linux patches available on your Linux web server. Speak to your web hosting company to get this updated. Clients hosting with us, our web servers have been patched as soon as the vulnerability was made public.
We strongly recommend running a manual server check if an automatic patch isn’t available to you. If you have any questions regarding the vulnerability or your solution please contact me and I can talk you through the solution.
For those interested in the more technical details behind the exploit, read all about Dirty COW.
by Michael Cropper | Nov 8, 2016 | Client Friendly, Security |
Unless you have been living in a cave over these last couple of weeks, you’ll probably have heard about the cyberattack that broke the internet for a few hours on several occasions. So what actually happened? It all starts with the DNS.
DNS stands for Domain Name System, in non-technical terms this is the technology that turns www.contradodigital.com into the servers IP address where your website files are hosted, for example, 178.238.139.113. There are many providers of DNS technology in use on the internet, with many providers using managed services of larger companies who have invested millions in the underlying hardware and infrastructure which enables the internet to work seamlessly. One of these companies providing DNS is called Dyn and here is where the cyberattack happened.
When the attack was happening, internet users in the following areas highlighted in the image below were unable to access many popular websites including websites like Twitter, SoundCloud, Spotify, Shopify and many more.
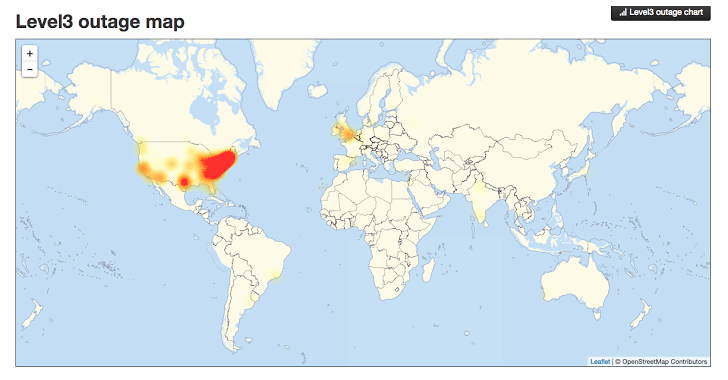
Image source: http://thehackernews.com/2016/10/dyn-dns-ddos.html
This is a significant part of the US and UK when customers and businesses could not access websites, meaning a significant drop in ecommerce sales for many organisations and a huge drop in productivity for those companies working in digital. For a system as large as the internet, which has been build with redundancy in mind, an attack of this scale is one of the worst we have seen to date and the seriousness of this means that businesses need to really step up in their cyber security efforts both large and small.
To read up more about the specifics of what a DDoS attack is and how this all happened, visit the Dyn website who have provided a write up on what happened.
Ultimately this attack was caused by hackers exploiting internet connected smart devices such as web cams and the likes. With the enormous rise in smart and internet connected devices available on the consumer market now, it is devices like this which are being exploited by hackers. When the software has been designed badly or built with un-updatable code or has been built with security holes in the code, it is this what is being exploited. Specifically using the Mirai software.
Distributed Denial of Service attacks are notoriously difficult to protect against, particularly on this scale with over 300,000 devices attacking a system. This is on the macro scale though and this really does just go to show that no matter how big you are attacks can happen to anyone. The even more worrying aspect is that this code has now been released open source so that the code is available to anyone wanting to exploit the same loophole.
The reality is that smaller and medium sized businesses are never reported on in the news. We deal with several hacked websites per month when businesses have failed to protect their self against cyberattacks. As a business owner you need to take cybersecurity seriously, and that means more than simply installing an antivirus and firewall on your laptops.
Picture this. You own a hotel. Imagine every door, windows, emergency exit and air vents into the building are ways of an attacker getting in. Not imagine your antivirus and firewall are your receptionists, blocking unwanted visitors in the building by locking the front door. Now imagine that all of the other doors, windows and vents in the entire building are left wide open for attackers to exploit. This is the reality that most businesses are dealing with without even realising. The software equivalent of this is that websites and web servers run outdated code, aren’t updated and active add security holes through using inefficient technologies and people to build systems. I cannot stress this enough, take cyber security seriously before you become the next victim. Sticking your head in the sand thinking that you will be fine will ultimately result in your business becoming the next headline. Be proactive.
Take advantage of our Free Digital Disaster Recovery Audit and test yourself on our Digital Evolution Score Card to see how advanced you are as an organisation and hence capable of dealing with problems. Better still, get in touch and we’ll talk you through the various options available for protecting your business, website and digital assets from cyberattacks.
by Michael Cropper | Sep 14, 2016 | Client Friendly, Security |
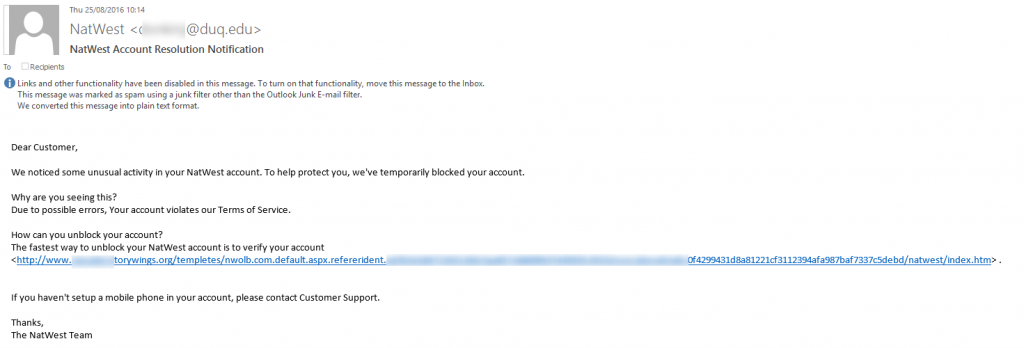
Probably one of the worst examples we’ve seen for a phishing email recently. Be aware though that these things do still catch people out. When you receive emails like this, always check the email address is from the correct website. Clearly in this case it isn’t. While this information cannot be trusted as this can be easily spoofed, many phishing emails like this one appearing to be from NatWest haven’t even bothered to add in the correct from email address.
Likewise, you will notice that the link they are asking you to click doesn’t go through to a NatWest website. Again, this information can be easily masked so you are best never to click on links in emails which appear to be suspicious. Always make sure that you open your web browser, go to the website directly without clicking on any links in emails to view notifications on your account. If the email was genuine, you will also have a notification within your account with the relevant information on.
Be safe.
by Michael Cropper | Sep 1, 2016 | Client Friendly, News, Security, WordPress |
Over the last few months there have been some really exciting changes happening in the website security world related to encryption. Something which now allows businesses of all shapes and sizes to take encryption seriously without the larger investment previously needed. Before we get into the nitty gritty, let’s take a look at what exactly SSL and HTTPS actually is and why it is important.
Google is to Flag Non-Secure Websites
Already SSL certificates are a factor in Google’s search algorithm, meaning that businesses using HTTPS are more prominent in Google’s search results when customers are searching. If this wasn’t enough for you to implement an SSL certificate, then eventually Google will be treating all websites like this that are not using HTTPS;
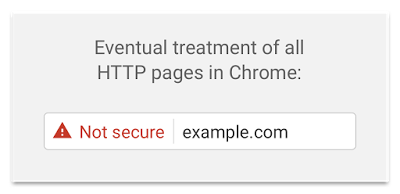
As a customer, what would you think if this warning came up when you were browsing your favourite websites? You would soon leave the website and begin to distrust the brand, right? Then the same is going through your customer’s minds too. Starting January 2016 Google will begin to flag insecure websites as not secure as can be seen below;
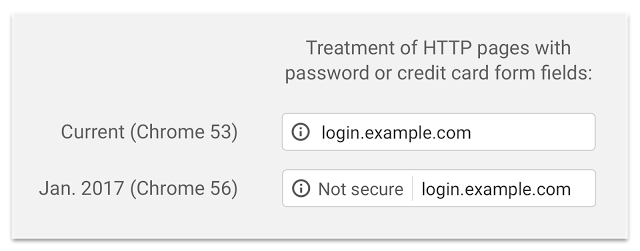
Now is the time to implement SSL on your websites to avoid the mad rush when Google turns this feature on. Read all about the finer details over on Google’s security blog.
Importance of SSL and HTTPS
Getting a little bit technical, SSL stands for Secure Socket Layer which turns the standard HTTP protocol used to access all websites on the internet into a secure connection. What this means in practice is that the connection between yourself typing www.contradodigital.com into the web browser and the web server is encrypted, meaning that no-one can listen in to what data is being sent/retrieved as you go about your day.
Take WordPress as a prime example, whenever you login to your WordPress website, if you are still using HTTP and not HTTPS then anyone listening in on the network can read your username and password in plain text, then use this data to hack into your website and do damage. So if you’re in a café or any other public place to access your website over HTTP, then it is relatively straight forward for people who know what they are doing to see your details. The same is true when you enter a username or password onto any other website on the internet, if they are using HTTP instead of HTTPS, then your password becomes visible to the world if someone is listening in on that network. SSL resolves these issues.
Anyone who is using any kind of login system on their website, whether this is simply for logging in administrators into your content management system, or running an ecommerce website, you should be using SSL. Previously an SSL certificate would have cost anywhere between £150 and £550 just for the certificate itself, plus the added cost of migrating your website from HTTP to HTTPS which can be a considerable cost in itself.
From a user perspective, implementing SSL simply means taking your website from HTTP;
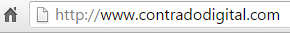
To HTTPS;
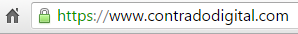
End to end encryption to secure your website.
Free SSL Certificates
Over recent months we’ve been experimenting with Let’s Encrypt, the new free certificate authority, the guys who generate the SSL certificates. Let’s Encrypt is backed by the likes of Facebook, Google, Cisco, Mozilla, Akamai, Automattic, Shopify, Sucuri, Hewlett Packard and many more. When Let’s Encrypt was first launched in April 2016, it was still very much in its early stages and quite buggy on a lot of platforms. Thankfully since then, it has become a lot easier to work with and hence is now something we’re recommending all businesses should take a look at for their own websites.

Practicalities
While Let’s Encrypt does bring free SSL certificates to everyone, it’s not quite as straight forward as just clicking a button and you’re good to go. As with all website and web server technologies, there are many moving parts with endless different setups and configurations. While the SSL certificates their self are free, implementing the initial Let’s Encrypt setup on your web server can be time consuming, or even in some cases, not even possible at the moment. Likewise, once you have claimed your free SSL certificate from Let’s Encrypt, you will likely need to implement various bits of website work to ensure SSL works correctly throughout the website.
Thankfully, we’ve got this town to a tee. Anyone hosting their website with us and running WordPress, we can implement this in no time at all, so get in touch so we can implement your free SSL certificate with minimal investments associated with the implementation of this. For anyone else, drop us an email anyway and we can review your current setup to see if it is capable of implementing the free SSL certificates from Let’s Encrypt.
For anyone brave enough to have a go their self, here are a few handy resources on some of the technical aspects in the background;
But the likelihood is that you’re not going to be able to implement this yourself, nor should you try if you aren’t competent as you can do some serious damage if you do things wrong. If your current web hosting partner or website team isn’t capable of implementing this or the technology isn’t up to scratch, then it’s probably time to review your current web hosting options;
Update – May 2017
As mentioned when initially publishing this blog post, companies need to act now to avoid losing potential customers.
Google Will Warn Potential Customers Not To Contact You in October….Act Now…
Google has been encouraging website owners to move towards a secure and encrypted internet for over 12 months now and they believe they have given website owners enough time to implement encryption technologies on their website to use SSL, i.e. when people view your website they view https://www.contradodigital.com rather than http://www.contradodigital.com. This means that the connection is encrypted and your customers data is secure when they are submitting things like credit card information or personal information on contact forms.
Unfortunately many websites are still not taking cyber security seriously which is why Google is taking the next step in October. In essence what this change will mean is that if you have not implemented an SSL certificate on your website by this time, anyone wanting to contact you through the contact form on your website using Google Chrome (the most popular web browser in use…) will be told that your website is ‘Not Secure’ which will put potential customers off from entering their details and contacting you. You need to act now to prevent your website being listed as Not Secure to your customers.
Here’s how your Contact Us page will look when people are about to fill out their details. Ask yourself, would you fill in a contact form on a website if you saw this warning message?

Here is an animation of what your contact form would do when people start entering in information;

What you need to do…
If you haven’t implemented an SSL certificate on your website to date, then you need to do so as soon as possible. This can be a relatively straight forward thing to do, or something a little more complex which depends on the technology you’re using in the background. Don’t worry about that though as we have implemented a lot of these for businesses over the last few years across a range of technologies.
Even better, SSL certificates are now FREE which is great as they would previously have set you back several hundred pounds for the certificate alone. So simply drop me an email directly and we can schedule some time in to implement this for you, michael.cropper@contradodigital.com
by Michael Cropper | Jul 25, 2016 | Client Friendly, Security |
Beware of the latest phishing email scam that is going around imitating a PayPal policy update. While PayPal often do send out similar emails, their terms and conditions are written as such that any updates are accepted by default so you never have to accept any new terms and conditions they announce.
The email;
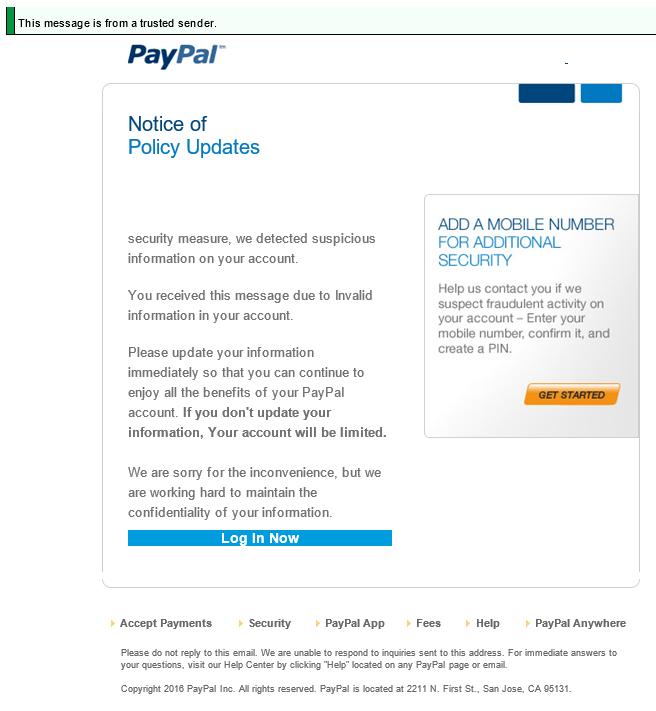
While this email looks genuine on quick glance, when you hover over the links, you notice that they do not go to www.paypal.com or www.paypal.co.uk, instead they go elsewhere to a phishing website. Thankfully if you did click the link in the email accidentally, if you are using a modern web browser, you are alerted to this attack;
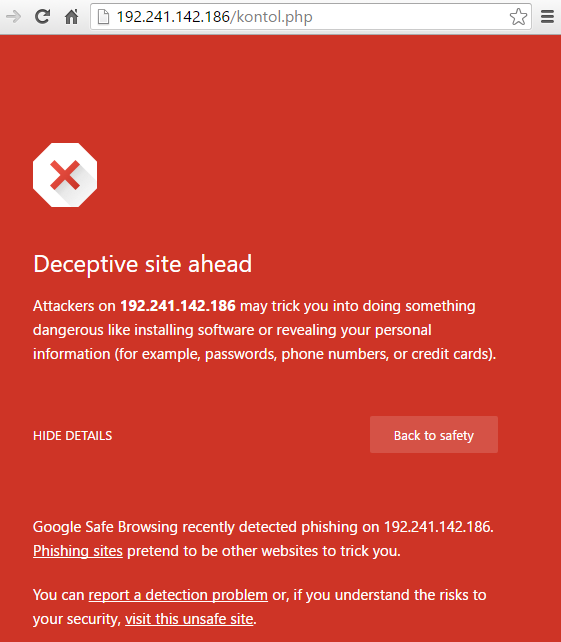
Another key aspect to notice in the original email is the recipient details which clearly don’t look genuine. While many aspects of this data can be easily faked, when the scammer hasn’t bothered to fake this data, it is easy to spot these kind of attacks;
As always, never click on suspicious links in emails and instead visit the website directly where you will find a notification if this is a genuine email.











