by Michael Cropper | Feb 26, 2018 | Security |
Phew! You can relax now.
We’ve started to see a report in spikes in porn blackmail emails come through from various people over the last few days. These emails have been coming through on corporate email addresses generally and with corporate email addresses often being added onto personal mobile phones that often younger members of the family use, this has had a few people concerned. But it’s ok, don’t worry. This is a scam.
When I investigated one of the emails it was clear that the scanners were playing on people’s sense of fear with the demand often being along the lines of;
“Tiсket Details: ECW-209-57819
Email: [REDACTED]
Camera ready,Notification: 21.02.2018 06:08:59
Status: Waiting for Reply 20xuVaAy8A0f64wMnKmJkL1FrF5Ky39Fu1_Priority: Normal
****************************************************************************
hi.
If you were more careful while playing with yourself, I wouldn’t worry you. I don’t think that playing with yourself is really awful, but when all colleagues, relatives and friends get video record of it- it is undoubtedly [bad for u.
I placed virus on a web-site for adults (with porn) which was visited by you. When the object press on a play button, device starts recording the screen and all cameras on your device begins working.
Moreover, my virus makes a dedicated desktop supplied with key logger function from ur device , so I was able to get all contacts from ya e-mail, messengers and other social networks. I’ve chosen this e-mail because It’s your corporate address, so you must read it.
I think that 330 usd is pretty enough for this little misstep. I made a split screen video(records from screen (interesting category ) and camera ooooooh… its awful AF)
So its your choice, if u want me to erase this сompromising evidence use my bitсoin wаllеt аddrеss: 1Lt4tLxQmZruKic23FYdAycB9a3GgTaacN
You have one day after opening my message, I put the special tracking pixel in it, so when you will open it I will know.If ya want me to show u the proofs, reply on this letter and I will send my creation to five contacts that I’ve got from ur device.
P.S. You can try to complain to cops, but I don’t think that they can solve ur problem, the inquisition will last for several months- I’m from Estonia – so I dgf LOL”
Sounds legit, right? Well, aside from the obvious spelling mistakes, grammatical errors and unsociable hour to be sending such a threatening email, sure.
Thankfully with a bit of investigation we can see that the IP address where this email is coming from is, 188.40.100.212, which is based in Germany with a German web hosting company, not Estonia. And while it is possible to send emails from different locations with relative ease, this one just doesn’t seem to stack up. As when you view the IP address in your web browser, you notice the default cPanel page which shows you that the website does not exist. Now for those of you who know cPanel well, you’ll also know that you can visit www.example.com/cpanel to get to the login page, and likewise, you can do the exact same from an IP address, so 188.40.100.212/cpanel also takes you to the login page.
Also from knowing cPanel very well, I also know how to secure cPanel, and I also know that many people who use cPanel do not secure it correctly and with minimal testing, it is clear that there is no brute force protection technology in place on this “hackers” web server – ironic. So with handy little scripts designed specifically to brute force your way into a cPanel account, should you decide to ‘research’, this is a relatively straight forward thing to do on insecure web servers.
You’ll also notice the Bitcoin wallet listed where you can deposit the “ransom”, yet when you check the transactions against that Bitcoin wallet, you’ll also notice that this wallet has never had any Bitcoins transferred in or out of the account. Another sign that this is clearly a fraudulent email – and that the people behind this scam aren’t that successful.
All in all, this looks to be what’s known as a ‘script kiddie’ in the industry, i.e. someone who clearly thinks they know more than they really do. Now as a non-teckie, this email still can be rather intimidating. Thankfully with a bit of know-how, you can start to spot these ever increasing range of tactics used by the scammers.
Something to bear in mind for all the script kiddies out there… It’s one phone call to the authorities and they’ll be speaking to your web hosting company to get your contact details. In this particular instance I investigated, this appeared to be from a hacked website, so as always – keep your website and web server secure before a hacker finds a vulnerability. It is so easy to find and exploit vulnerabilities when you know what you are looking for…
On a final note, web browsers are designed with security in mind. Web browsers simply cannot access the hardware of your device without your express permission, regardless of the content you are browsing. As a simple example, uploading an image to a website, you’ll notice that this brings up a popup for your standard operating system controlled dialogue box. What this means in layman’s terms is that control has been handed over to the underlying operating system to determine how to proceed with the request and the web browser is waiting for a response to know what to do next. The web browser simple cannot turn on your camera remotely without you agreeing to it.
As a sub-note though, if a hacker manages to find a way to install a program on your device, then they will likely have full access to everything. So keep that in mind too…
by Michael Cropper | May 15, 2017 | Client Friendly, Security |
Firstly to clarify, what happened to the people who have been impacted by the latest WannaCry Ransomware attack such as those having hospital appointments cancelled and suchlike is nothing short of a tragedy. I really do feel for the end users who have been impacted by this latest cyberattack that has spread so far and wide and has impacted people on a personal level. This rant below is not about the people who have been affected, this is about those organisations who quite simply have failed to protect their self against such threats due to poor security measures. Everything related to the latest WannaCry Ransomware attack is preventable.
Companies and organisations that have been impacted by the latest WannaCry Ransomware, I have one thing to say to you and that is that I honestly have no sympathy if you have been breached and have quite frankly failed to protect yourself. It’s the same situation whereby homeowners get burgled when they have left their front door unlocked and open, whereby car owners get their cars stolen in Winter when they have left the keys in the car running on the driveway for a chancer to take advantage of, whereby a car driver fails to wear their seatbelt, has an accident and injures their self. All of these things are preventable and most importantly, we all know what we should be doing in these situations so when the correct procedures and best practice aren’t followed, should we really have sympathy for those who have attacked by the latest WannaCry Ransomware?
Within 48 hours of being launched, WannaCry impacted over 200,000 computers in over 150 countries around the world. The WannaCry Ransomware was exploiting a known vulnerability in the Microsoft Windows operating system, a vulnerability that has been known about for at least 2 months publicly and much longer within the National Security Agency (NSA) which actually built a tool named EternalBlue which WannaCry is built upon.
This is a known vulnerability that organisations have simply failed to take seriously and act upon which is why I have no sympathy for those organisations impacted by the latest WannaCry Ransomware. The latest versions of Windows run automatic security updates and patches which means that as soon as vulnerabilities are known about, they are patched almost immediately and help to keep your company and organisation safe. In the situation with many of the NHS breaches, this comes down to computer systems and hospital hardware such as X-Ray Scanners running unsupported, vulnerable and unpatched versions of Windows XP. That’s right, an operating system that was launched in 2001, over 16 years ago, and has not been officially supported by Microsoft for over 3 years.
While organisations that have been impacted may indeed WannaCry while dealing with the fallout from this latest cybersecurity threat, personally I have no sympathy with those affected. Cybersecurity protection is a choice we all make. You choose either to protect yourself, or you choose not to. Clearly the right choice here is to protect yourself.
Have you been impacted by the latest WannaCry Ransomware? Then we can certainly help you resolve the issues your organisation is having and get you onto the right track to become a cybersecurity aware and secure organisation. Get in touch if you need help taking proactive measures to secure your business against cyberattacks.
You may have noticed, we take cybersecurity threats seriously which is why we ensure IT and web based systems are secure from cyberattacks. We help organisations like yours become a cyber aware and cyber secure organisation. We can only do so much ourselves, which is why we encourage organisations of all sizes to start investing in cybersecurity protection before you are the latest in a long line of statistics about the disruption and impact from cybercrime. If you don’t have the skills in-house to deal with issues like this, you need to be working with a company like ourselves to secure your business. You need to take the first step and reach out to IT security companies and ask them to help you to secure your systems. I write blog posts like this not to criticize and point fingers, but to raise awareness and encourage more businesses and organisations to become more cyber aware and secure.
We also sent out the email below to our mailing list who receive priority information on threats like this. If you aren’t subscribed yet, then make sure you fill out your email address in the footer.
WannaCry Ransomware and the NHS
As you will have likely seen on the news over the weekend there has been one of the largest Ransomware attacks in recent history which completely took offline the NHS, many local authorities throughout the UK and has now spread to over 150 countries around the world impacting over 10,000 organisations. As a business, you need to ensure you are protecting yourself against threats like this.
What is WannaCry and Ransomware?
WannaCry is the name of this specific piece of software that has been created by hackers which belongs to a group of cyber security threats known as Ransomware. Ransomware is when a piece of software holds your company to ransom by encrypting all of your data on your entire company systems (file systems, email systems, in-house servers etc.) and you can only gain access to this again by paying these hackers money for them to unlock your files. Money is often paid in cryptocurrencies such as Bitcoins as they are untraceable.
How to Protect Yourself Against Ransomware
Protection against threats like this is actually relatively straight forward. You must be taking proactive steps on a weekly basis to keep your IT systems up to date, patched and secure. Do not expect that either your IT person or your IT Support provider is handling this for you, you need to know exactly what processes are in place for these areas of protecting your business.
Secondly, staff training is extremely important to protecting your business from cyberattacks such as Ransomware. No matter how secure your IT systems are, if unaware staff open an attachment on an email or click on a link they believe to be genuine, this can bring down your entire company systems and stop work altogether. This in itself is not only costly in the form of not being able to work, it is even more costly to resolve situations like this after they have happened. Prevention and protection is always cheaper than the cure.
What to do Next?
As a business you should be investing in regular IT security support which helps to protect your systems from threats like this. This doesn’t have to break the bank either, the systems and technologies that are available today are a fraction of the cost they were 10 years ago which makes them affordable to businesses of all sizes. – Find out more
As a business you should be investing in regular staff training on cyber security threats to minimise the risk of one of your members of staff causing a damaging cybersecurity breach within your company based on lack of awareness. A workshop run at your premises or one of our group based sessions are prefect for companies of all sizes. – Find out more
We cannot stress this enough, when you are proactive dealing with cybersecurity threats, your organisation will be safer. Simply sticking your head in the sand and thinking that it will never happen to you has proven on many occasions to be a very bad decision and virtually always results in a cyberattack happening.
by Michael Cropper | Feb 17, 2017 | Security |
For those of you using Microsoft Exchange for your email platform, be aware of the latest phishing email going around telling you that you;
“Your email have exceeded maximum disk quota allocated, we require re-activation to continue using mail service…. Our system will automatically purge out mail that have exceeded quota, to avoid this please kindly follow our instruction.”
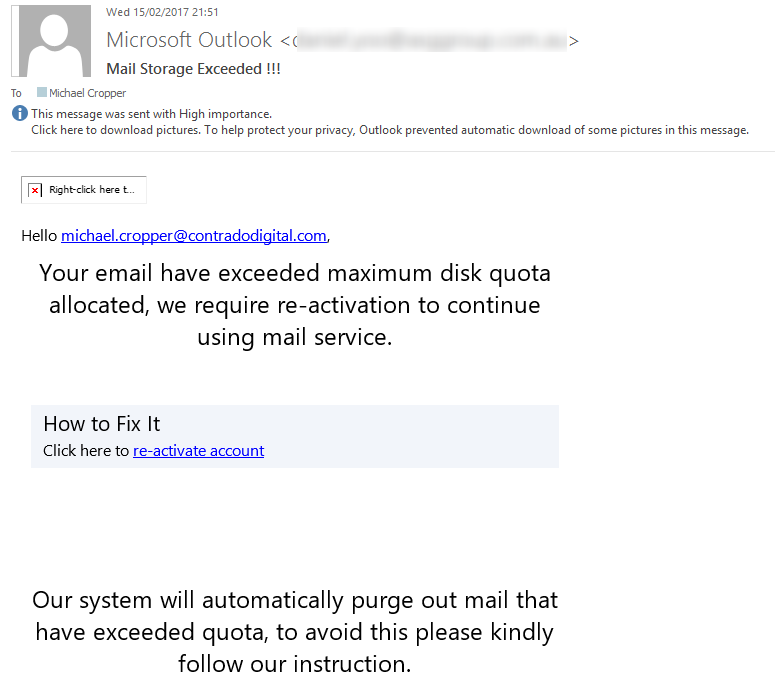
As always, if any email looks suspicious, never click on any links that you see. In this particular case, the email ‘from’ address which has been blurred out above is clearly not from Microsoft, it was from an IT company based in Australia. It is likely they have been hacked their self then their web server was used as a way to attack more businesses. While the ‘from’ email address can be easily faked, when the from email address is clearly not from where you would expect, this is a clear sign that this email is fake. In addition to this, when you hover over the link in the email, the link URL is to a strange website with a lot of random characters which is another clear sign that this email is a phishing scam.
Always keep an eye out for phishing scams like this
by Michael Cropper | Feb 14, 2017 | Client Friendly, Security, SEO, WordPress |
You may have recently received an email from Google Search Console warning you that your website is being flagged as Non-Secure Collection of Passwords as can be seen below;
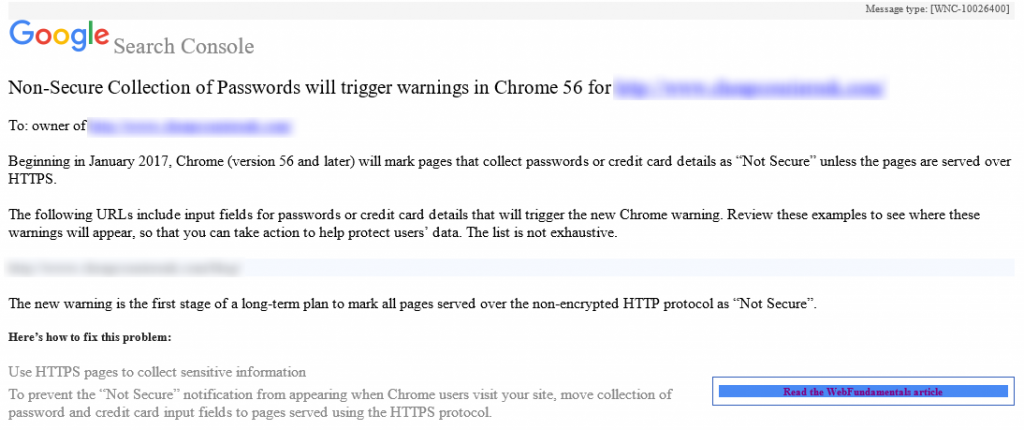
If you have been sent a message like this, you need to act before it is too late. You have received this message because your website is running over HTTP instead of HTTPS on pages that you collect sensitive information. Whenever either you or your users enter sensitive information on any website using HTTP, i.e. http://www.contradodigital.com/wp-login.php then this information can be seen in transit by anyone listening in on the network.
What you need to do
The solution to resolving these warnings is actually relatively simple. If you want to have a go at this yourself, then make sure you claim your free SSL certificate and update your website accordingly. If you need any help implementing this then get in touch and we can help you with the process.
by Michael Cropper | Feb 9, 2017 | Client Friendly, Security, WordPress |
Google Search Console, formerly called Google Webmaster Tools, has started to inform WordPress website owners when security updates are available. This is a great effort by Google to help website owners and businesses keep their websites safe and secure with regular WordPress security maintenance.
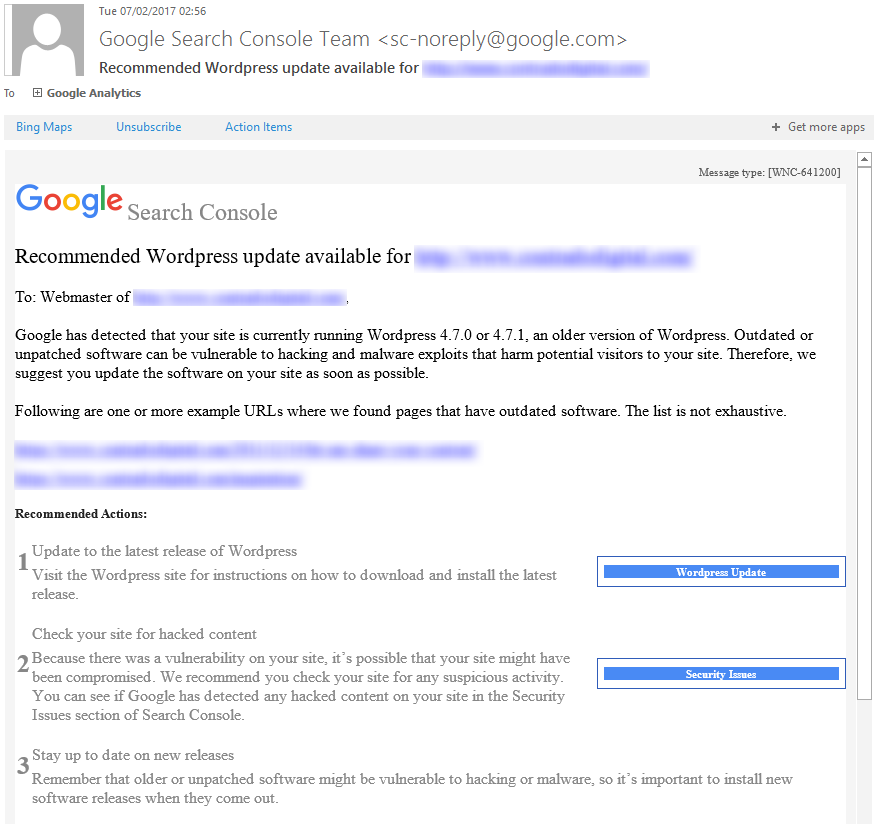
While this is a great step forward, as a business owner you must not wait until you see these kinds of messages from Google until you take action to update your WordPress website. These messages are purely focused at the WordPress Core files, which is only a small part of WordPress security. If you think of security like you would with a building, imagine WordPress Core files being your front door. Just because your front door is locked, it doesn’t mean that you haven’t left your windows, back doors, side doors and garage unlocked and open. It is the same concept with WordPress security. You must be taking proactive measures to protect your website against hackers.
If you aren’t sure how to go about dealing with WordPress security, then fear not, drop us an email and we can talk you through the options available.

by Michael Cropper | Feb 9, 2017 | Client Friendly, Security, WordPress |
WordPress 4.7.2 is now available. This is a security release for all previous versions and we strongly encourage you to update your sites immediately. If you are unsure how to deal with WordPress security updates, get in touch and we can manage your WordPress security updates for you.
WordPress versions 4.7.1 and earlier are affected by three security issues:
- The user interface for assigning taxonomy terms in Press This is shown to users who do not have permissions to use it. Reported by David Herrera of Alley Interactive.
WP_Query is vulnerable to a SQL injection (SQLi) when passing unsafe data. WordPress core is not directly vulnerable to this issue, but we’ve added hardening to prevent plugins and themes from accidentally causing a vulnerability. Reported by Mo Jangda (batmoo).- A cross-site scripting (XSS) vulnerability was discovered in the posts list table. Reported by Ian Dunn of the WordPress Security Team.
- An unauthenticated privilege escalation vulnerability was discovered in a REST API endpoint. Reported by Marc-Alexandre Montpas of Sucuri Security. *
Thank you to the reporters of these issues for practicing responsible disclosure.
Download WordPress 4.7.2 or venture over to Dashboard → Updates and simply click “Update Now.” Sites that support automatic background updates are already beginning to update to WordPress 4.7.2.
Thanks to everyone who contributed to 4.7.2.
* Update: An additional serious vulnerability was fixed in this release and public disclosure was delayed. For more information on this vulnerability, additional mitigation steps taken, and an explanation for why disclosure was delayed, please read Disclosure of Additional Security Fix in WordPress 4.7.2.




