by Michael Cropper | Apr 22, 2015 | Events |
We recently attended the Cyber Security Conference which was looking at the enormous problem that is cyber security, or should I say cyber crime. Cyber security is a bigger issue than most businesses realise, with central government classifying cyber security as a Tier 1 threat, the same level as terrorism. Yet we will see many businesses not taking adequate steps to secure their businesses. At Contrado Digital, our focus is on digital marketing, websites and other online topics. These naturally are open to many of the issues related to cyber security which often aren’t in the realms of the traditional IT Support type companies who manage the physical security related to network routing and more. There is naturally a cross over between the two areas, which is why we have started to cover this area a little more recently as it is an area that is not understood that well by most businesses, particularly those within the SME bracket.

Security Investment
One phrase that you should really think about is this; Good security will cost you, bad security will cost you more. This is one that resonated with me at the conference as I can relate to this on many occasions when businesses have come to us with problems related to security. On many occasions we hear businesses say things along the lines of “We don’t have access to our own website, webserver or social media accounts and the web developer has gone AWOL, what can we do?” This is security and is a big risk for your business.
Coming back to the phrase, good security will cost you, bad security will cost you more, what can you realistically do in this situation? Well, you have to start again in many instances which is a much more costly approach than simply getting the right processes and training in place within your business from the start. This specific example is the reason why we have put together a free resource for keeping tracking of your digital assets with our Digital Assets Tracker document.
Going beyond the basics, it is hugely important to look at the training requirements within your organisation and invest in a creating a security culture. To the point whereby local IT support company Holker IT have recently launched a campaign to educate businesses with their Think Before You Click campaign. So many issues related to security are human error due to lack of knowledge, so make sure your staff have been trained up and are aware of the latest security threats that could cause a serious problem for your business.
Planning for Problems
No system is infallible, this is an unfortunate fact of life when dealing with computer systems, programs, hardware and processes reliant on human input. So what are your plans for when something does happen? What, you don’t have any? Far too many businesses don’t have any serious plans in place for when cyber security issues arise and simply have the opinion that it will never happen to them. I’m sure the people involved with the recent celebrity scandal thought the same…
The reality is that something will happen and you need to plan for when this does and put in procedures that can mitigate against issues. This broadly falls into three categories;
- How will you deter it?
- How will you detect it?
- How will you respond to it?
Thinking through the potential problems that could occur and planning for this will mean you have a much more secure business, lower your chances of financial and reputational damage along with allowing you to focus on what is important, growing your business.
Let’s look at a few examples to put things into perspective.
Distributed Denial of Service (DDoS) Attack
A cyber criminal has decided to attack your website with a Distributed Denial of Service attack (DDoS) and your website is no longer accessible. Read up about an example a while ago that we had to deal with. This was only a small scale attack in the grand scheme of things, what if it had been bigger?
How will you deter it? – While you cannot control if someone has decided they are going to attack your website, you can put in place measures to pro-actively block attacks. For example, with WordPress, there are plugins such as Limit Login Attempts and Akismet that will help to deter DDoS attacks which should be installed along with other professional security plugins which we also use.
How will you detect it? – What systems have you got in place to detect when this is happening? Or do you simply find out when you happen to check your website and realise that it is not working? How many enquiries or lost ecommerce sales have you had during this time? Any reputable web hosting company will have pro-active monitoring in place to alert you to when your server falls over due to hugely increased loads, allowing you to respond in a timely manner and deal with the issue promptly.
How will you respond to it? – What are you actually going to do to stop the attack? Simply sit it out and watch it unfold until it hopefully stops? If your web server has already fallen over, then there is little you can do until you can gain access again. Depending on the technical configurations you have in place along with the nature of the attack, it may be possible to divert traffic to another server, allowing you to get access to your main server and implement security changes such as blocking all traffic from a certain IP address or a group of IP addresses. Then once the change has been made, you can redirect all traffic back to your main server which should reduce the load and allow your websites to function normally again. Again, certain hosting companies pro-actively monitor for DDoS attacks and intervene by automatically blocking suspicious traffic on the network level before they even get to your web server which is great.
WordPress Brute Force Password Hacking
A cyber criminal has decided to hack into your website by guessing your administrator password. They have wrote a basic computer programme which loops through common passwords before running through a password generator script in a logical order to find your password.
How will you deter it? – There are plugins available for WordPress which will automatically block anyone who attempts to login to your website using the ‘Admin’ username which is the WordPress default. You should always be using a unique Administrator username which isn’t ‘Admin’ or ‘Administrator’. Pick something unique for you which is hard to guess. This means that any hacker has to guess both the username and password which is exponentially more difficult. In addition, certain plugins will automatically block IP addresses from accessing your website if they guess any password incorrectly a set number of times.
How will you detect it? – There are plugins available for WordPress that will automatically send you an email when an IP address has been blocked from logging in to your website due to too many failed login attempts. This can alert you to a problem and can help to highlight the start/stop of any attack that is happening.
How will you respond to it? – Responding to a hacking attempt which is aiming to guess your password is about being pro-active. If you have a password which is ‘password123’ then this isn’t the most secure password in the world and could be cracked by a computer programme within minutes. Always make sure you are using strong usernames and passwords for your WordPress websites to avoid vulnerabilities.
WordPress Plugin Vulnerability Exploits
A cyber criminal has noticed that you are running your website from the world’s most popular content management system WordPress and has decided that you are a good target. They know that many WordPress website owners don’t update their plugins and patch security holes regularly so have decided that you would be a good target for hacking into. After all, they already have a list of what has been patched by comparing the older versions of plugins to the latest versions of plugins so they have an easy shopping list of exploits to try and hack into your website with.
How will you deter it? – What activities are you doing to avoid leaving your WordPress website open to vulnerability exploits? You are keeping all of your plugins, themes and WordPress core up to date, right? This is the absolute minimum that you should be doing to avoid cyber criminals taking over your website. You really need to be thinking about subscribing to a service that will detect threats in real time which will keep you much safer.
How will you detect it? – How will you detect if your website has been exploited? Often many website owners and businesses have no idea that their website has been infected by some malicious code that has been placed there which could be hiding in the background working away. When a cyber criminal exploits a vulnerability in your website, this usually isn’t about changing the visual appearance of your website, this is usually about hiding code away so that you think everything is fine. Again, there are many services available that will scan your core WordPress files for vulnerability exploits and raise a flag if a piece of unexpected code is found which is likely to be an exploit.
How will you respond to it? – Now you have managed to detect the problem, getting rid of the problem can be a whole other challenge. Depending on the complexity of the hijacked code will determine how easy or difficult this is to get rid of. Prevention is always better than dealing with these types of problems when they occur since many sophisticated pieces of code will hide their self from your view and only show to search engines and only under certain circumstances.
Summary Planning
The three examples above are just the basics when it comes to protecting your website from attacks. The real focus should be about planning for problems so your website doesn’t become one of the statistics around hacked websites.
Do not think that this will never happen to you, it will. Cyber criminals often don’t care about you or your website specifically, they simply create computer programmes which crawl the internet (in the same way Google does) to find all target websites (i.e. WordPress and others). Once they have found their targets, they simply automatically test each website for known vulnerabilities. At this level, which isn’t hard to achieve, hacking is basically a spectator sport. Press ‘go’ on your script and you just sit back and wait for a report to be generated for every websites in your target list (bearing in mind that WordPress powers over 23% of websites on the entire internet….that’s a lot of targets…) with a list of which vulnerabilities they are open to.
You cannot rely on any kind of enforcement here to get you out of a sticky situation. The unfortunate reality is that you are on your own (or getting help from us…). There are so many potential problems beyond the three examples above that people need to protect their website from this is an area that needs serious attention. With many hacking attempts coming from over-seas, there is very little jurisdiction that can help dealing with problems after they have occurred.
Thankfully we offer WordPress Security services which are designed to keep your website safe and secure so that you are prepared and don’t fall victim. Always think about any potential problem in relation to your own website and business; How will you deter it? How will you detect it? How will you respond to it? Reactive approaches are too late. Proactivity is key.
Scale of the Problem
A recent report from Trustwaves in the form of their Global Security Report found some interesting statistics including;
- 45% of data thefts are for non-payment card data
- Ecommerce made up 54% of assets targeted
- Point of sale (POS) breaches accounted for 33% of investigations they did
- Retail was the top compromised industry- likely due to the nature of data they keep about customers in databases
- 85% of the exploits detected were from 3rd party plugins
- Weak passwords contributed to 31% of breaches
- 96% of investigated applications had one or more serious security vulnerabilities
- Ecommerce and website breaches rose by 5% since 2012 – I believe this figure is hugely understated
- The average number of vulnerabilities identified per application was 14
- 100% of mobile applications tested contained at least one vulnerability
- 71% of victims did not detect the breach their self
- The average number of days from initial intrusion to detection was a whopping 87 days
When terms such as application, website, ecommerce etc. are used. This is often the same underlying programming languages and exploits that are being used in different ways. Do not think that these problems are isolated to a specific area.
Going beyond simply looking at the enormous numbers behind these problems. There are services available online including Shodan which has a fantastic blog covering lots of ‘interesting’ topics. The service classifies itself as ‘The search engine for internet-connected devices’. I.e. Internet of Things, Webcams, Buildings, Websites, Refrigerators, Power Plants and more. I’m not going to talk about the technologies behind how all of this works here as this gets a little geeky. What is important is that for only $9 / month, you can literally search the world of internet connected devices for vulnerabilities.
So again, are you confident that you are protected and have the right procedures in place?
Physical Hardware
There was a lot of talk at the conference along the lines of physical hardware security and network security. A little beyond our area of expertise, but a couple of interesting points around this which may resonate;
- You need solutions at the network security level, not just software solutions. For example if you have a multi-site office, it was recommended that you look at using MPLS to protect your data in transit.
- Your home broadband provider can see what devices you have connected to your router. If you regularly work from home or you have a home based business, you may prefer to keep your business hardware private from prying eyes. It was recommended to always have an additional router between the router provided by your ISP and your devices so that wandering eyes cannot see what is connected to your network from further afield. For example, imagine a call centre employee noticing that your house appears to have 15 iPads, 3 iMacs, 12 iPhones and 4 smart TVs all connected to the router you were provided (yes, you have a big house…). This would certainly be more of a target for thieves. Whereas if they only saw that 1 additional router was connected to the network then they would simply look elsewhere.
Information Governance Programme
While this may sound like the setup for much larger multi-national organisations, it is important to recognise the importance for all businesses large and small. Larger organisations often rely on smaller organisations as part of their supply chain in one way, shape or form which are often a target for attackers due to the often more relaxed approach to information security.
Recently central government made the new Cyber Essentials certification a mandatory requirement for anyone bidding for central government contracts which highlights the importance. From many speakers at the event from mammoth organisations and senior positions in government were reiterating the importance of security throughout the entire supply chain. To the point whereby many large organisations are putting together training programmes for their supply chain to educate them about the standards that they expect.
Information governance is not just data, it is a lot more than that. It includes areas such as;
- Information risk management
- Information management
- Intellectual property
- Knowledge management
- ICT
All of which touch on some of the terms that you may be more familiar with; SaaS (Software as a Service), BYOD (Bring Your Own Devices), cloud, virtualisation, employees, customers, contractors, outsourced people/companies. Looking at this in more technical terms to see what areas are often attacked when you look at data assets;
- Data at rest – For example data in the many databases you use within your business across multiple systems
- Data in use – For example data that is stored in caches, security certificates, data in RAM
- Data in motion – For example networked systems
A professor from Lancaster University talked through a range of the options hackers have to access systems ranging from the obvious technical areas such as HTTP, downloads/uploads, SQL injection to the ones people often don’t think about as much such as FTP clients, emails/webmail, instant messaging, peer-2-peer, file sharing, HTTPS, STFP, SSH, VPN, protocol tunnelling including DNS, HTTP, ICMP, Box, Dropbox, image steganography, VOIP, routing control packets and more. Some of these you will likely never have heard of if you aren’t that technical, but I guarantee that you will be using them in some way without even realising.
The graphic below from Lancaster University highlights some of the common methods used;
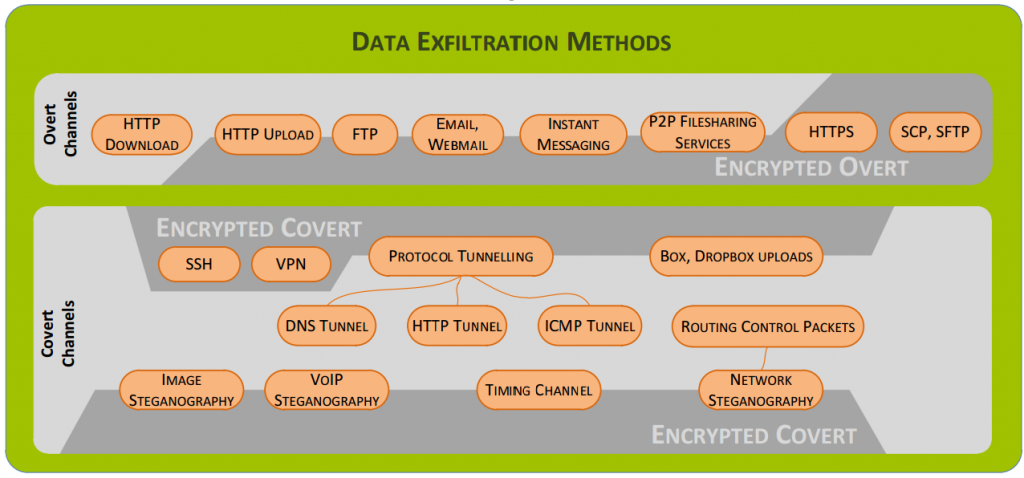
Again, all of these acronyms above are used by the many of the technologies that you use on a daily basis without even realising.
Summary
Cyber security is a serious problem. These are just some of the highlights from the excellent conference. Many other topics were discussed, although I feel that the people speaking about the more exciting topics would prefer if some of this information wasn’t boasted about so this has been left out for obvious reasons.
By far, the largest problem around cyber security at the moment which was reiterated by all at the event was around lack of education of the real problem that is out there. Many businesses simply have the opinion that it will never happen to them, or they are too small for people to care. This is simply not the case and I hope this blog post covering a small selection of the many exciting topics discussed will help to highlight some of the issues and what businesses can do to protect their-self online.
If you would like to discuss any website security related issues then get in touch or see how our website security audit could help. There are many aspects related to cyber security and we are by no means an expert on every aspect. With dealing predominantly with websites and online ‘things’ this is where our focus lies including details around specific technologies and systems. If you ask us about something that is a little outside of the scope of our expertise, then we can certainly put you in touch with one of our many contacts that are more suitable to support your business.
Resources, Sources and Further Reading
UK National Security Strategy: https://www.gov.uk/government/uploads/system/uploads/attachment_data/file/61936/national-security-strategy.pdf
UK Cyber Security Strategy: https://www.gov.uk/government/uploads/system/uploads/attachment_data/file/60961/uk-cyber-security-strategy-final.pdf
HMG Security Policy Framework: https://www.gov.uk/government/uploads/system/uploads/attachment_data/file/316182/Security_Policy_Framework_-_web_-_April_2014.pdf
Introduction to Cyber Security course from the Open University: http://www.open.edu/openlearn/futurelearn/cyber-security
Cyber Streetwise: https://www.cyberstreetwise.com/
10 Steps to Cyber Security: http://www.gchq.gov.uk/press_and_media/news_and_features/Pages/Relaunch-10-Steps-to-Cyber-Security.aspx
Competitive analysis of the UK cyber security sector: https://www.gov.uk/government/uploads/system/uploads/attachment_data/file/259500/bis-13-1231-competitive-analysis-of-the-uk-cyber-security-sector.pdf
Information Security Breaches Survey 2014: http://www.pwc.co.uk/assets/pdf/cyber-security-2014-technical-report.pdf


































