by Michael Cropper | Jun 10, 2015 | SEO |
A Short Story About… series, sharing stories about epic fails related to digital marketing, web design, technology choices and more. All designed to make you aware of what can happen when you work with the wrong people and an inexperienced digital agency. Remember the importance of working with the right digital agency.
Sharing these real life stories with you allows you to review your own setup to make sure you aren’t making the same rookie mistakes. Sharing is caring and it also makes our life easier when you speak with us about increasing your revenue through digital marketing and technology.
Look at our new shiny website!
The story starts here…. We received an email from a business owner who mentioned that they had passed on our details to another business owner related to some work that they needed support with. Nothing too strange here, we get this all the time.
Naturally, when we receive requests such as this, we have a quick nosey around to get a feel for the website, digital marketing channels, technologies in use and more. Based on this quick analysis we soon get a feel for where the business is at when it comes to how digitally advanced they are, or aren’t, as the case may be.
Having already heard of the business that had been referred to us, we already knew that the website was in development with another agency (sorry, we’re not going to name and shame here, but we shall say that they are local to us…). Based on this, we had a quick look around the new website;

Website X
Initial Investigations
One of the key areas we investigate is to see what technology the website has been built with and ultimately decide if we even want to get involved with helping the business. Depending on the technology used and other factors, we often turn down work that is just too far gone to help and there is no budget for a complete rebuild. Often bad decisions in the past can lead to costly solutions in the future, often which businesses don’t have budgets for re-doing something. Thankfully though, there is generally something we can help with in one way shape or form.
We always recommend the right solutions for businesses, it’s unfortunate that this ethos isn’t the same for all agencies, with many often using poorly configured technology, custom built technology and everything in between. Hence, why businesses come to us when things have gone wrong elsewhere and they are looking for a good solution that is truly suitable for their long term needs. As a caveat, there are a lot of good agencies around alongside ourselves and we can quite happily point you to them. It is also true, as many businesses are painfully aware, that there are a lot of charlatans around too.
So, while investigating what technology was powering the website, we soon noticed a login button on the website;

So we had a quick look at the login page to see if this resembled any of the common content management systems around;
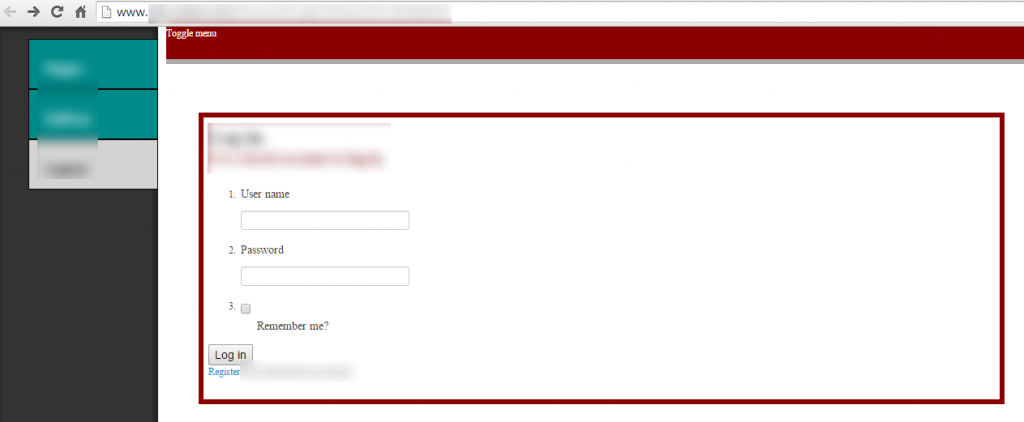
And what do we see here, a nice “Register” button, so we investigated a little further;

Ooohh, that looks like a nice easy registration form, so we tested a little further…;
- Username: test
- Password: test123
- Confirm password: test123
Surely any content management system or website worth it’s weight in salt would handle guest registrations in a graceful and secure way? Well, no, and this is where we were really shocked to see how bad this system has actually been built in terms of security. After registering a user using the form available on the website for anyone to see, we went back to the login page from earlier and tested these details;
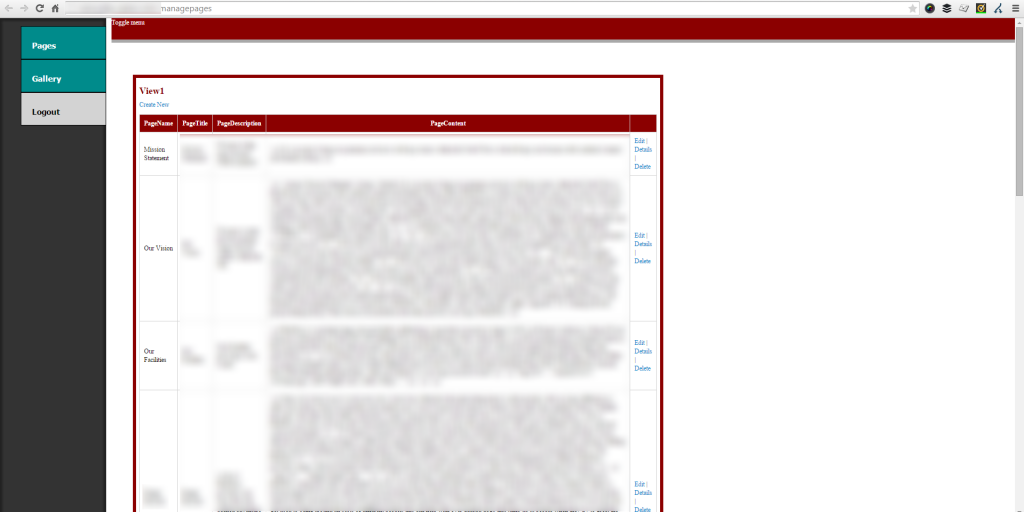
And here we are, straight into the administration area where we can edit the content of the website as we choose. Adding content, deleting content, uploading images in the gallery, addling links to websites of our choosing and more. To test that we do indeed have the right privileges, we added (and then immediately removed) a piece of content to the website which was visible once we updated this;
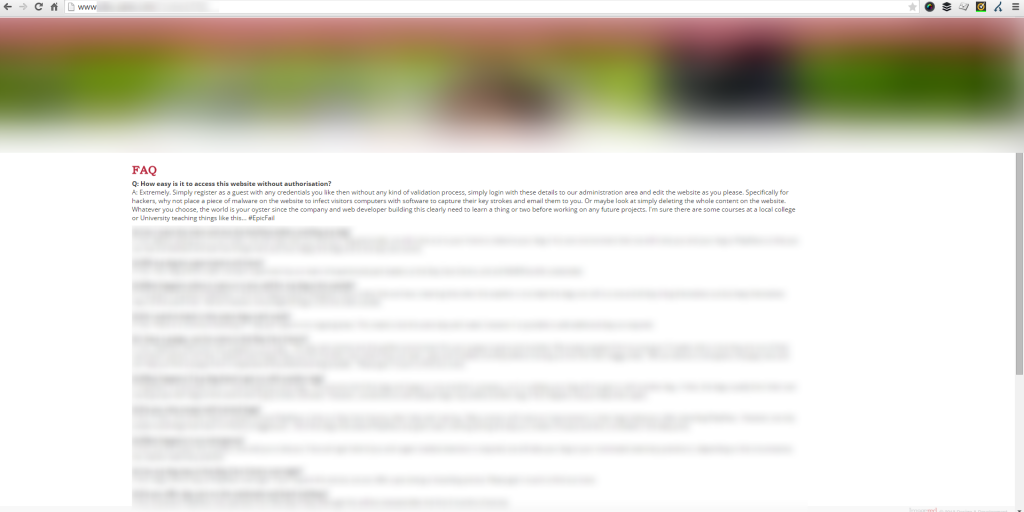
(Click for larger view)
The above isn’t the actual content that was added to the website for obvious reasons. It was simply a number “1” which was added to one of the sentences then removed immediately. The above image is purely for illustrative purposes and to emphasise the point.
It is extremely worrying that a website can be built with no security in place at all. This process took no more than 5 minutes to investigate, test and access the admin area. Imagine what we could do in 10 minutes…
Now if someone came along who had an axe to grind or was looking to infect websites with malware and other code, this would be extremely easy thing to do. Not only could this result in the website being blacklisted from Google, your own website visitors and customers could be infected with viruses or your website could be (unknowing to you) part of a bot net that is hacking many websites around the world.
This blog post is not designed to show how good we are when it comes to identifying security issues related to websites (although we aren’t too bad at that…), this blog post is designed to highlight how easy security issues can occur when you are using either the wrong technology, incorrectly configured technology, sloppy web developers or an agency who clearly has no idea what they are doing.
For any website or web application, security should be embedded from the start of the project and clear testing throughout to ensure that only those who have access to the administration area do have access to it. Security is not an added extra, this is your own business and website that we are talking about. An area that you have clearly worked hard on and one that will no doubt have been a reasonable investment. Don’t get caught out with rookie mistakes.
Imaging if the administration area contained a list of all of your customers who had registered with your website? Or if this contained personal sensitive information in unencrypted form, names, email addresses, phone numbers or heavens forbid credit card details? Such a simple mistake can turn into an enormous problem. All preventable when you are working with the right people who have the skills, knowledge and experience to do the job properly.
Technology
For reference, the technology behind the website in this case study was running the following;
- IIS 8 Web Server
- Net / ASP.Net MVC Framework (this is where the problem and solution lie, allowing anyone to view the user registration page and allowing the default user to be created as an Administrator)
- Google Hosted Libraries
- jQuery
- Fancybox
Incorrectly configuring technology is one of the most common pitfalls related to website security. It is so important that you are working with a well-respected company who have staff with a wealth of experience and capable of preventing issues like this occurring.
The Solution
Throughout this blog post, the company has remained masked and is not identifiable in any way for obvious reasons. The company has also been notified and their agency is working on a solution as a priority. We believe in responsible disclosure, which is why we have published these findings, to avoid others falling into the same trap.
For reference for the developers working on this solution, if any pointers are needed, a quick Google search for the solution came up which may be quite useful;
Please also have some form of robust security processes in place within your business to prevent this happening again in the future. Please also check all of your other clients who you have built websites for in this same fashion, as this could also need fixing on their website too. Again, it is extremely simply to gather a list of websites built by the same agency where this problem could also exist;
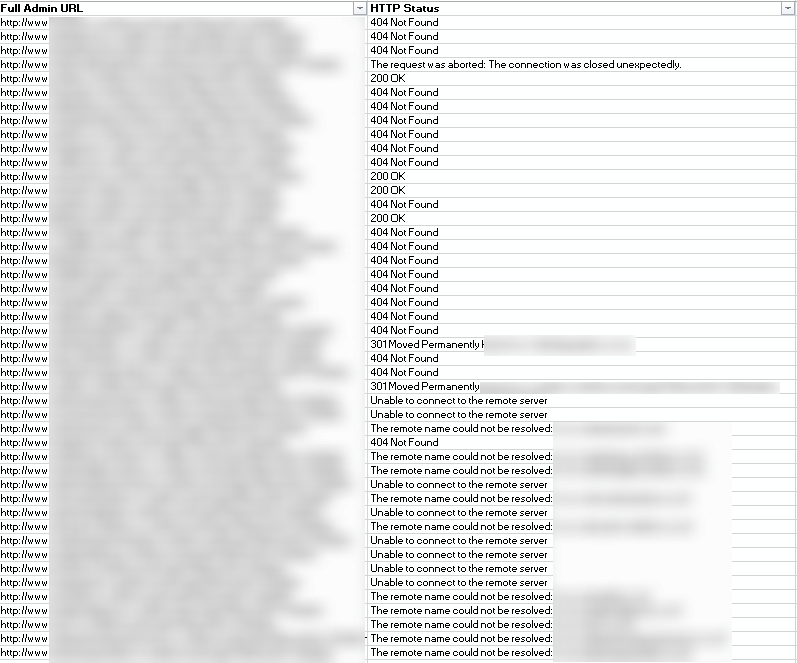
For anyone looking to do harm, this could turn into a reputational nightmare for the agency involved along with causing all of the businesses involved an awful lot of lost revenue if this was exploited fully by a hacker before a solution was implemented. Staff training, for both technical and non-technical users is key in this area to ensure that problems are identified before other people find them and exploit them.
Summary
As mentioned at the start, it is essential that you are working with the right digital agency who is capable of delivering projects in a secure fashion. Simply working with the cheapest company, the company who can talk the best talk or the company who manages to convince you that their solution is the best one over all of the others just isn’t going to cut it. As a business owner or decision maker, it is ultimately your responsibility that you are working with well-respected agencies who know what they are doing.
If you are concerned by the contents of this blog post, if you are questioning your current supplier or are generally concerned about the security of your digital assets, then get in touch. Cyber security is a hot topic for a reason, it is hugely important to protect the future of your online presence and more.
The learning point: Ensure your website registration process doesn’t allow new users to access parts of the website they shouldn’t. In this example, using a well-respected content management system would have prevented this issue altogether. Many website builds do not require any fancy custom built content management system solution, popular platforms such as WordPress or Magento are often perfect for the job.
by Michael Cropper | May 13, 2015 | SEO |
Seriously, have we reached full capacity? I’m speaking specifically about traditional broadband connections, not fibre broadband. The ‘old’ broadband running on the copper lines from the exchange. It seems that this technology is well and truly full, at least based on personal experience and that of anecdotal evidence from speaking with other people in a similar situation.
To put this into context, previously the internet connection at home has been more than adequate for a good number of years based on the type of activities within the household. More recently, since our old provider was bought out by a larger provider and my personal working habits have changed slightly, I am starting to question if the current broadband infrastructure has reached full capacity and I’m putting the question out there, have you noticed any difference recently in your home non-superfast internet speeds?
Superfast Internet
The rollout of superfast broadband throughout the UK is absolutely needed, but have we gone far enough with the rollout? The current superfast broadband rollout is what is technically known as Fibre to the Cabinet, FTTC for short. In lay-person speak, this means that there is now a fibre connection from your local telephone exchange to the little green box at the end of your street.
Traditionally, this part of the journey was powered using copper wire. This is a problem due to the laws of physics. Transferring data (i.e. your internet connection) is significantly faster through a fibre optic cable than through the old copper wires. Hence why the rollout of fibre broadband was essential as data usage has significantly increased over recent years with the growth of services such as Netflix, YouTube, Amazon Prime, Tesco Blink, Xbox Live, Online Gaming and more.
But I question whether we have gone far enough with the upgrades and whether we actually have a long term solution in place for the growing data requirements for home and business users. The current superfast broadband rollout is a significant improvement which has implemented the improvements to part of the line as can be seen below;
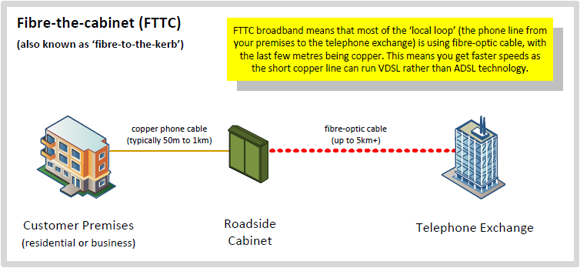
Source: http://www.thinkbroadband.com/guide/fibre-broadband.html
What you will notice is that this isn’t the whole picture. There is part of the connection which is still using the older technology, which is the part of the connection between your green box and your home. For office use, this generally is not a problem as there is either a leased line to the premises or similar technology making the internet connection truly superfast. For some users, and most importantly, the growing remote and flexible workers as part of your workforce, this is actually a large problem. Personally, there is rarely a working day that is the same, with work being completed in various locations depending on the plan for the week. Which means that for myself personally, I could be experiencing internet connections with down streams nearing 100 mb/s or as poor as 2mb/s with continuous dropouts depending on the time of the day. While this doesn’t interrupt any activities, it does require a little more planning, a backup plan in place at all times in the form of mobile data, oh, and the forced upgrade to a fibre connection – more on that later though.
Speaking based only on anecdotal evidence, on a traditional broadband connection at home, the evidence is clear, broadband connectivity issues starting around 3:30pm, peaking around 5pm, starting to tailor off around 7pm. What I’m talking about here is when the internet connectivity gets so bad that it is not possible to load a website or connect to the internet. After a lot of thought on the topic, the only conclusion that I can make based on this is that children are arriving home from school at around 3:30pm, accessing all of the on-demand services, clogging up the internet then going to bed around 7pm. Thinking through many options that could be causing this, along with endless discussions with home broadband technical departments working to ‘resolve the issue’ (and failing miserably), it is clear that the old provider was not able to fix the issue which I believe to be related to the capacity crunch that we are all experiencing invisibly at the minute.
The Capacity Crunch
The next step of my personal story is that we are moving to superfast fibre broadband at home, not out of a want for faster speeds as for home use, traditional broadband used to be absolutely fine for our needs as a home user. No, we are moving to a superfast fibre connection out of necessity. As part of the process, one comment from the new supplier struck a cord and made me think about what has actually happened with the recent broadband rollout project within the UK. The comment was that the new provider is going to have to send out an engineer to the green box and flick us on to fibre.
So in summary, unless you are paying directly for a fibre connection, you simply aren’t benefiting from this new technology. Call me a cynic, but this does seem a little strange why home users aren’t automatically switched over to this upgrade when they already often paying reasonably hefty prices for basic usage, on the whole – and that the project was part funded (50/50) by the European Union through the European Regional Development Fund and local authorities throughout the UK.
The question I came to ask myself was whether we, as home consumers, were being forced down a paid upgrade route when the reality is that the current service being provided simply isn’t up to scratch and is not fit for purpose. The copper pipe is already full which is causing service issues for those people using traditional broadband technology.
Another topic in this area, which we will cover in more depth in another blog post is the difference between broadcast technology (i.e. your live TV) VS streaming technology (i.e. anything over the internet). We’ll look at the technical details a little more another time, for now, the key point is that broadband technology is a first-come-first-serve basis, meaning that if there is a certain amount of capacity on the old copper lines, then whoever uses the capacity first wins and those who aren’t quick enough lose out. All of this is clearly a little more complex than this in the background and simply put, those closer to the exchange have priority over the bandwidth. Meaning that the further away from your local exchange you are, the further down the pecking order you are when it comes to getting your fair share of bandwidth and often those further out are left with the crumbs at the end.
It may be no surprise to you based on the tone of this blog post that we aren’t quite sat next to the local exchange at home. Never the less, we also aren’t tens of miles away either. Traditional broadband has been (up until recently) and should be absolutely fine for our needs, yet it isn’t. Instead, a forced ‘upgrade’ to a fibre service is required to maintain basic connectivity to the home, not to get 200x the speed we currently get.
The Cloud
Putting this into context from a business perspective as a whole, more and more staff are requesting home and flexible working options for various reasons. The image I came across on LinkedIn recently resonated with a lot of people and really does go to show where business and the idea of ‘work’ is heading;
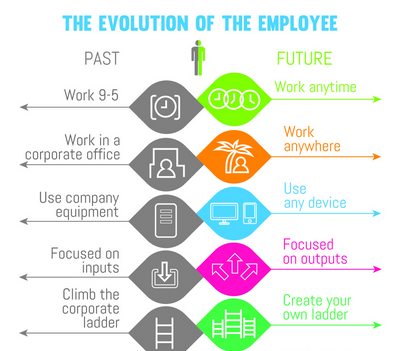
Attribution required: If this is your image, get in touch and we’ll credit you accordingly J
The concept of a modern day working environment requires an unbelievable robust internet connection throughout the UK that can be enjoyed by all. One that I do not believe we have. The recent upgrades are a step in the right direction but we need more.
As more businesses migrate their entire business to the cloud for all of the benefits this brings, the key to all of this working seamlessly is a robust internet network. With accounting software, project management software, research tools, file storage systems, customer relationship management systems and more all being contained within the cloud. This all only works with a fantastic internet connection throughout all parts of the data journey.
The Reality for Many
While this blog post may seem like a little rant against poor performing internet speeds at home, it isn’t. I’ve had that spat directly with the current provider on Twitter J No, this blog post is to highlight the issue that many people are currently experiencing yet there seems to be no real long term solution to this growing problem. Sure, we have had a significant improvement in the form of fibre broadband throughout the UK, but this is not going to last and quite frankly this rollout is not the inclusive Britain that we all aim to strive for. The ever increasing costs related to basic services, and I do include internet in this category, needs addressing and a real solution needs to be identified.
Browse through the swarms of people on Twitter complaining every day about broadband connection speed problems from all suppliers à https://twitter.com/search?f=realtime&q=slow%20broadband&src=typd. Backing up personal anecdotal evidence. This isn’t just the reality for a small number of people, this is a problem impacting an awful lot more people than those just voicing their opinions on Twitter.
Again, putting this into perspective, when comparing home broadband speeds directly with data speeds when connecting to the internet via a mobile phone provider, it is clear there is an issue with the technology;
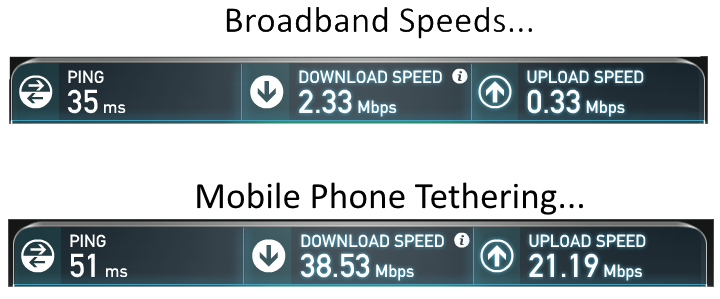
The mobile data tariffs are just way too expensive currently to warrant permanent connectivity through mobile phone networks. Although maybe this is a longer term solution and the reason why BT is looking to buy EE for £12.5 billion, the largest and fastest mobile network throughout the UK.
The Future
So where do we go from here? Clearly this is a problem where the solution is a little more involved than my thoughts in a blog post. With some interesting blog posts coming from BT on the matter recently, the issue is clearly already under discussion;
“BT’s head of optical access, Professor Andrew Lord, who will take part in the conference said: “It’s the first time we have had to worry about optical fibres actually filling up. We could expand the network by laying more cables but the economics of that do not work and it would increase power consumption. Prof Lord added that a possible solution to the problem would be to ration internet access, where household consumers and businesses would be charged for the amount of data they use.” – Source (5th May 2015)
“The internet will not need to be rationed in the future because of a “data capacity crunch”, according to a leading scientist from telecoms giant BT.” – Source (11th May 2015)
Whatever the solution, it is clear that more needs to be done by all the key players in this market to address these issues, and fast. Many web services are seeing exponential growth in data usage as consumer behaviour shifts from broadcast to on-demand services which is only going to grow further. Couple this with the future horizon in an internet connected world with the Internet of Things, we have a serious crunch approaching in my opinion.
This is purely my personal opinion on where we are at currently and where we are heading. It would be great to hear your thoughts on the topic and share your experience in the comments. Do you think the internet has reached full capacity? Do you think we are heading for a capacity crunch? Or are you simply loving your new fibre broadband speeds streaming series after series of the latest dramas on Netflix?
by Michael Cropper | Apr 27, 2015 | SEO |

Last week we were invited to a party Google was throwing for those involved in the recent Grow Local campaign which was designed to help businesses get on board with Google AdWords. Held at Europe’s largest multi-arts and conference venue, the Barbican in London. We had a great evening full of goodies, entertainment and a bit of technology, naturally.
-

-
Google Squishy Toy
-

-
Grow Local Activities
-

-
Grow Local….get it…
-

-
Google Goodies!
-

-
Grow Local Activities
-

-
Fish
-

-
Thirsty fish
-

-
Garden Party at the Barbican
-

-
Create your own garden from food
-

-
Google Boxes
-

-
Google Grub
-

-
Make a wish…
-

-
Some wishes never come true…
-

-
General ambiance
-

-
General ambiance
-

-
General ambiance
-

-
Allotments
-

-
Google Grow Local Party
-

-
The Barbican
Google Cardboard
We got our hands on our own Google Cardboard Virtual Reality system. And yes, it is just a piece of cardboard, but it is a cool piece of cardboard. The pack comes in flat-pack mode and allows you to place your smartphone into the device and be truly immersed in a virtual world. Hold the device and look in any direction and control your movements inside the virtual world. Ride on virtual rollercoasters, view museum exhibits, walk around stately homes, fly over Chicago or get immersed in a Paul McCartney concert (if that’s your thing…). Our custom paint job on the Google Cardboard leaves a little to be desired…
-

-
Google Cardboard
-

-
Google Cardboard
-

-
Google Cardboard
-

-
Google Cardboard
-

-
Google Cardboard
-

-
Google Cardboard
-

-
Google Cardboard
-

-
Google Cardboard
-

-
Google Cardboard
-

-
Google Cardboard
by Michael Cropper | Apr 22, 2015 | SEO |
We recently attended the Cyber Security Conference which was looking at the enormous problem that is cyber security, or should I say cyber crime. Cyber security is a bigger issue than most businesses realise, with central government classifying cyber security as a Tier 1 threat, the same level as terrorism. Yet we will see many businesses not taking adequate steps to secure their businesses. At Contrado Digital, our focus is on digital marketing, websites and other online topics. These naturally are open to many of the issues related to cyber security which often aren’t in the realms of the traditional IT Support type companies who manage the physical security related to network routing and more. There is naturally a cross over between the two areas, which is why we have started to cover this area a little more recently as it is an area that is not understood that well by most businesses, particularly those within the SME bracket.

Security Investment
One phrase that you should really think about is this; Good security will cost you, bad security will cost you more. This is one that resonated with me at the conference as I can relate to this on many occasions when businesses have come to us with problems related to security. On many occasions we hear businesses say things along the lines of “We don’t have access to our own website, webserver or social media accounts and the web developer has gone AWOL, what can we do?” This is security and is a big risk for your business.
Coming back to the phrase, good security will cost you, bad security will cost you more, what can you realistically do in this situation? Well, you have to start again in many instances which is a much more costly approach than simply getting the right processes and training in place within your business from the start. This specific example is the reason why we have put together a free resource for keeping tracking of your digital assets with our Digital Assets Tracker document.
Going beyond the basics, it is hugely important to look at the training requirements within your organisation and invest in a creating a security culture. To the point whereby local IT support company Holker IT have recently launched a campaign to educate businesses with their Think Before You Click campaign. So many issues related to security are human error due to lack of knowledge, so make sure your staff have been trained up and are aware of the latest security threats that could cause a serious problem for your business.
Planning for Problems
No system is infallible, this is an unfortunate fact of life when dealing with computer systems, programs, hardware and processes reliant on human input. So what are your plans for when something does happen? What, you don’t have any? Far too many businesses don’t have any serious plans in place for when cyber security issues arise and simply have the opinion that it will never happen to them. I’m sure the people involved with the recent celebrity scandal thought the same…
The reality is that something will happen and you need to plan for when this does and put in procedures that can mitigate against issues. This broadly falls into three categories;
- How will you deter it?
- How will you detect it?
- How will you respond to it?
Thinking through the potential problems that could occur and planning for this will mean you have a much more secure business, lower your chances of financial and reputational damage along with allowing you to focus on what is important, growing your business.
Let’s look at a few examples to put things into perspective.
Distributed Denial of Service (DDoS) Attack
A cyber criminal has decided to attack your website with a Distributed Denial of Service attack (DDoS) and your website is no longer accessible. Read up about an example a while ago that we had to deal with. This was only a small scale attack in the grand scheme of things, what if it had been bigger?
How will you deter it? – While you cannot control if someone has decided they are going to attack your website, you can put in place measures to pro-actively block attacks. For example, with WordPress, there are plugins such as Limit Login Attempts and Akismet that will help to deter DDoS attacks which should be installed along with other professional security plugins which we also use.
How will you detect it? – What systems have you got in place to detect when this is happening? Or do you simply find out when you happen to check your website and realise that it is not working? How many enquiries or lost ecommerce sales have you had during this time? Any reputable web hosting company will have pro-active monitoring in place to alert you to when your server falls over due to hugely increased loads, allowing you to respond in a timely manner and deal with the issue promptly.
How will you respond to it? – What are you actually going to do to stop the attack? Simply sit it out and watch it unfold until it hopefully stops? If your web server has already fallen over, then there is little you can do until you can gain access again. Depending on the technical configurations you have in place along with the nature of the attack, it may be possible to divert traffic to another server, allowing you to get access to your main server and implement security changes such as blocking all traffic from a certain IP address or a group of IP addresses. Then once the change has been made, you can redirect all traffic back to your main server which should reduce the load and allow your websites to function normally again. Again, certain hosting companies pro-actively monitor for DDoS attacks and intervene by automatically blocking suspicious traffic on the network level before they even get to your web server which is great.
WordPress Brute Force Password Hacking
A cyber criminal has decided to hack into your website by guessing your administrator password. They have wrote a basic computer programme which loops through common passwords before running through a password generator script in a logical order to find your password.
How will you deter it? – There are plugins available for WordPress which will automatically block anyone who attempts to login to your website using the ‘Admin’ username which is the WordPress default. You should always be using a unique Administrator username which isn’t ‘Admin’ or ‘Administrator’. Pick something unique for you which is hard to guess. This means that any hacker has to guess both the username and password which is exponentially more difficult. In addition, certain plugins will automatically block IP addresses from accessing your website if they guess any password incorrectly a set number of times.
How will you detect it? – There are plugins available for WordPress that will automatically send you an email when an IP address has been blocked from logging in to your website due to too many failed login attempts. This can alert you to a problem and can help to highlight the start/stop of any attack that is happening.
How will you respond to it? – Responding to a hacking attempt which is aiming to guess your password is about being pro-active. If you have a password which is ‘password123’ then this isn’t the most secure password in the world and could be cracked by a computer programme within minutes. Always make sure you are using strong usernames and passwords for your WordPress websites to avoid vulnerabilities.
WordPress Plugin Vulnerability Exploits
A cyber criminal has noticed that you are running your website from the world’s most popular content management system WordPress and has decided that you are a good target. They know that many WordPress website owners don’t update their plugins and patch security holes regularly so have decided that you would be a good target for hacking into. After all, they already have a list of what has been patched by comparing the older versions of plugins to the latest versions of plugins so they have an easy shopping list of exploits to try and hack into your website with.
How will you deter it? – What activities are you doing to avoid leaving your WordPress website open to vulnerability exploits? You are keeping all of your plugins, themes and WordPress core up to date, right? This is the absolute minimum that you should be doing to avoid cyber criminals taking over your website. You really need to be thinking about subscribing to a service that will detect threats in real time which will keep you much safer.
How will you detect it? – How will you detect if your website has been exploited? Often many website owners and businesses have no idea that their website has been infected by some malicious code that has been placed there which could be hiding in the background working away. When a cyber criminal exploits a vulnerability in your website, this usually isn’t about changing the visual appearance of your website, this is usually about hiding code away so that you think everything is fine. Again, there are many services available that will scan your core WordPress files for vulnerability exploits and raise a flag if a piece of unexpected code is found which is likely to be an exploit.
How will you respond to it? – Now you have managed to detect the problem, getting rid of the problem can be a whole other challenge. Depending on the complexity of the hijacked code will determine how easy or difficult this is to get rid of. Prevention is always better than dealing with these types of problems when they occur since many sophisticated pieces of code will hide their self from your view and only show to search engines and only under certain circumstances.
Summary Planning
The three examples above are just the basics when it comes to protecting your website from attacks. The real focus should be about planning for problems so your website doesn’t become one of the statistics around hacked websites.
Do not think that this will never happen to you, it will. Cyber criminals often don’t care about you or your website specifically, they simply create computer programmes which crawl the internet (in the same way Google does) to find all target websites (i.e. WordPress and others). Once they have found their targets, they simply automatically test each website for known vulnerabilities. At this level, which isn’t hard to achieve, hacking is basically a spectator sport. Press ‘go’ on your script and you just sit back and wait for a report to be generated for every websites in your target list (bearing in mind that WordPress powers over 23% of websites on the entire internet….that’s a lot of targets…) with a list of which vulnerabilities they are open to.
You cannot rely on any kind of enforcement here to get you out of a sticky situation. The unfortunate reality is that you are on your own (or getting help from us…). There are so many potential problems beyond the three examples above that people need to protect their website from this is an area that needs serious attention. With many hacking attempts coming from over-seas, there is very little jurisdiction that can help dealing with problems after they have occurred.
Thankfully we offer WordPress Security services which are designed to keep your website safe and secure so that you are prepared and don’t fall victim. Always think about any potential problem in relation to your own website and business; How will you deter it? How will you detect it? How will you respond to it? Reactive approaches are too late. Proactivity is key.
Scale of the Problem
A recent report from Trustwaves in the form of their Global Security Report found some interesting statistics including;
- 45% of data thefts are for non-payment card data
- Ecommerce made up 54% of assets targeted
- Point of sale (POS) breaches accounted for 33% of investigations they did
- Retail was the top compromised industry- likely due to the nature of data they keep about customers in databases
- 85% of the exploits detected were from 3rd party plugins
- Weak passwords contributed to 31% of breaches
- 96% of investigated applications had one or more serious security vulnerabilities
- Ecommerce and website breaches rose by 5% since 2012 – I believe this figure is hugely understated
- The average number of vulnerabilities identified per application was 14
- 100% of mobile applications tested contained at least one vulnerability
- 71% of victims did not detect the breach their self
- The average number of days from initial intrusion to detection was a whopping 87 days
When terms such as application, website, ecommerce etc. are used. This is often the same underlying programming languages and exploits that are being used in different ways. Do not think that these problems are isolated to a specific area.
Going beyond simply looking at the enormous numbers behind these problems. There are services available online including Shodan which has a fantastic blog covering lots of ‘interesting’ topics. The service classifies itself as ‘The search engine for internet-connected devices’. I.e. Internet of Things, Webcams, Buildings, Websites, Refrigerators, Power Plants and more. I’m not going to talk about the technologies behind how all of this works here as this gets a little geeky. What is important is that for only $9 / month, you can literally search the world of internet connected devices for vulnerabilities.
So again, are you confident that you are protected and have the right procedures in place?
Physical Hardware
There was a lot of talk at the conference along the lines of physical hardware security and network security. A little beyond our area of expertise, but a couple of interesting points around this which may resonate;
- You need solutions at the network security level, not just software solutions. For example if you have a multi-site office, it was recommended that you look at using MPLS to protect your data in transit.
- Your home broadband provider can see what devices you have connected to your router. If you regularly work from home or you have a home based business, you may prefer to keep your business hardware private from prying eyes. It was recommended to always have an additional router between the router provided by your ISP and your devices so that wandering eyes cannot see what is connected to your network from further afield. For example, imagine a call centre employee noticing that your house appears to have 15 iPads, 3 iMacs, 12 iPhones and 4 smart TVs all connected to the router you were provided (yes, you have a big house…). This would certainly be more of a target for thieves. Whereas if they only saw that 1 additional router was connected to the network then they would simply look elsewhere.
Information Governance Programme
While this may sound like the setup for much larger multi-national organisations, it is important to recognise the importance for all businesses large and small. Larger organisations often rely on smaller organisations as part of their supply chain in one way, shape or form which are often a target for attackers due to the often more relaxed approach to information security.
Recently central government made the new Cyber Essentials certification a mandatory requirement for anyone bidding for central government contracts which highlights the importance. From many speakers at the event from mammoth organisations and senior positions in government were reiterating the importance of security throughout the entire supply chain. To the point whereby many large organisations are putting together training programmes for their supply chain to educate them about the standards that they expect.
Information governance is not just data, it is a lot more than that. It includes areas such as;
- Information risk management
- Information management
- Intellectual property
- Knowledge management
- ICT
All of which touch on some of the terms that you may be more familiar with; SaaS (Software as a Service), BYOD (Bring Your Own Devices), cloud, virtualisation, employees, customers, contractors, outsourced people/companies. Looking at this in more technical terms to see what areas are often attacked when you look at data assets;
- Data at rest – For example data in the many databases you use within your business across multiple systems
- Data in use – For example data that is stored in caches, security certificates, data in RAM
- Data in motion – For example networked systems
A professor from Lancaster University talked through a range of the options hackers have to access systems ranging from the obvious technical areas such as HTTP, downloads/uploads, SQL injection to the ones people often don’t think about as much such as FTP clients, emails/webmail, instant messaging, peer-2-peer, file sharing, HTTPS, STFP, SSH, VPN, protocol tunnelling including DNS, HTTP, ICMP, Box, Dropbox, image steganography, VOIP, routing control packets and more. Some of these you will likely never have heard of if you aren’t that technical, but I guarantee that you will be using them in some way without even realising.
The graphic below from Lancaster University highlights some of the common methods used;
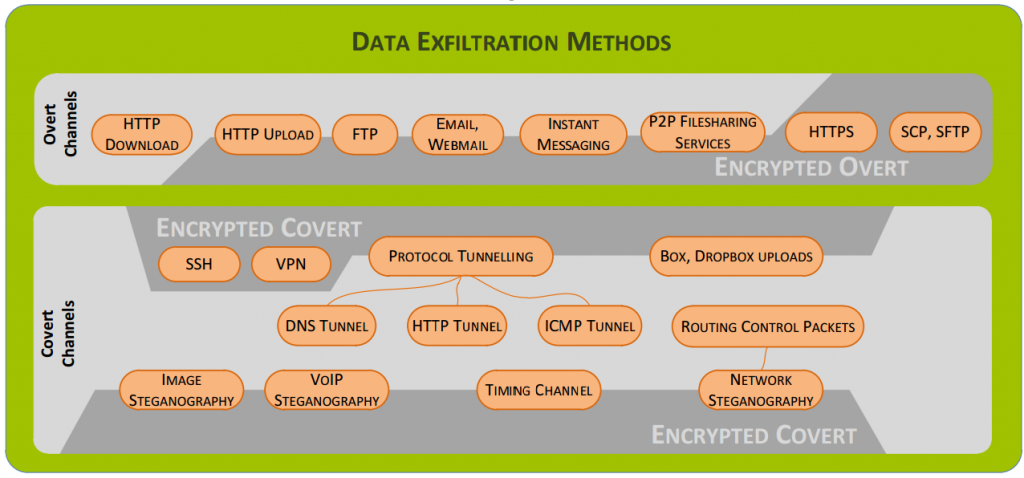
Again, all of these acronyms above are used by the many of the technologies that you use on a daily basis without even realising.
Summary
Cyber security is a serious problem. These are just some of the highlights from the excellent conference. Many other topics were discussed, although I feel that the people speaking about the more exciting topics would prefer if some of this information wasn’t boasted about so this has been left out for obvious reasons.
By far, the largest problem around cyber security at the moment which was reiterated by all at the event was around lack of education of the real problem that is out there. Many businesses simply have the opinion that it will never happen to them, or they are too small for people to care. This is simply not the case and I hope this blog post covering a small selection of the many exciting topics discussed will help to highlight some of the issues and what businesses can do to protect their-self online.
If you would like to discuss any website security related issues then get in touch or see how our website security audit could help. There are many aspects related to cyber security and we are by no means an expert on every aspect. With dealing predominantly with websites and online ‘things’ this is where our focus lies including details around specific technologies and systems. If you ask us about something that is a little outside of the scope of our expertise, then we can certainly put you in touch with one of our many contacts that are more suitable to support your business.
Resources, Sources and Further Reading
UK National Security Strategy: https://www.gov.uk/government/uploads/system/uploads/attachment_data/file/61936/national-security-strategy.pdf
UK Cyber Security Strategy: https://www.gov.uk/government/uploads/system/uploads/attachment_data/file/60961/uk-cyber-security-strategy-final.pdf
HMG Security Policy Framework: https://www.gov.uk/government/uploads/system/uploads/attachment_data/file/316182/Security_Policy_Framework_-_web_-_April_2014.pdf
Introduction to Cyber Security course from the Open University: http://www.open.edu/openlearn/futurelearn/cyber-security
Cyber Streetwise: https://www.cyberstreetwise.com/
10 Steps to Cyber Security: http://www.gchq.gov.uk/press_and_media/news_and_features/Pages/Relaunch-10-Steps-to-Cyber-Security.aspx
Competitive analysis of the UK cyber security sector: https://www.gov.uk/government/uploads/system/uploads/attachment_data/file/259500/bis-13-1231-competitive-analysis-of-the-uk-cyber-security-sector.pdf
Information Security Breaches Survey 2014: http://www.pwc.co.uk/assets/pdf/cyber-security-2014-technical-report.pdf
by Michael Cropper | Mar 24, 2015 | SEO |
We recently attended the Manchester Digital #DigitalRevolution conference hosted at AutoTrader in Manchester. The event, as usual, was another fantastic event full of insights from the digital world and how things are significantly changing for businesses of all shapes and sizes.
With the recent announcement of a £4,00,000 fund for Manchester to support the launch of Tech North, this is a clear commitment how the world is changing and how every businesses needs to adopt digital technologies throughout every aspect of their business. While this isn’t a huge sum of money, it is a great start and builds upon the work from many other digital organisations, groups and partners within the Greater Manchester region.
We first heard from a panel of speakers who took a step back in time to look at where we have come from and how we have got where we are now. Taking Google as the example in comparison to the dominant search engines of the time, Alta Vista and Lycos (if you can remember those!) and looking at how Google managed to gain such an enormous market share. Current data puts Google’s market share in the up at almost 90% which is unbelievable. The one thing they did though is make their search engine easy to use for people. While all other search engines at the time kept adding more features, functionality, content, widgets and other clutter to their homepage, Google kept things simple and just allowed people to search. After all, that is what their entire business model is built on so why get in the way of people searching? In addition to this, Google’s AdWords platform was, and still is, industry leading. To the point whereby there is no real competition to this for targeting potential customers searching for your products or services.
The discussions soon turned to the skills gap that every business currently faces related to digital technology. A topic of conversation at every Manchester Digital event. The point was made about continual learning and about how essential this is for anyone and any business touching on digital. If you don’t move, you get left behind. It really is as simple as this. Whether this is related to personal career development or as a business. The build it once and forget about it approach is not suitable and if this is still your approach, you will soon (if not already) be in a position whereby your website and digital assets are out of date. We take continual learning extremely seriously which is why we are always getting out and about to industry related events, conferences and exhibitions along with sharing our insights on our client friendly blog and our developer blog.
On a personal level for your staff, are you investing enough in their skills and career development? Most companies within the SME bracket aren’t. I’m sure you have heard the saying “What if we invest in training and people leave….What if we don’t invest in training and they stay….” This couldn’t be truer with how fast the digital world moves. We run regular digital training events and also run bespoke training sessions for your individual business needs which cover many of the topics and more listed on our events page.
Next it was reiterated about utilising all of the digital marketing opportunities open to your business, SEO, PPC, Email Marketing, Social Media, PR, Branding, Marketing and more. Simply doing things in silos isn’t going to cut it, there needs to be an integrated marketing approach across all channels.
It was also predicted that by 2020 we will have homes with no computers. To the point whereby regular devices around us would allow us to connect with the digital services seamlessly. We have already seen the proliferation of smartphones and how this has changed customers’ lives. Only last year, the BBC announced over 50% of their traffic to iPlayer and recently announced that now over 65% of traffic to the BBC website is now using a mobile or tablet device. This is an enormous change in a very short space of time. Which is one of the reasons why Google recently announced that they are going to be giving a boost in the search engines for mobile friendly websites and penalising websites that aren’t mobile friendly. This point was stressed to the point whereby if your website isn’t being built with a mobile first approach then it is soon going to be obsolete if people simply cannot use key functionality on your website. People are inherently lazy and don’t want to go back to their laptop or desktop computer to complete a task.
Another prediction, which I personally don’t agree with, but it was predicted that Facebook would lose 80% of their users within 5 years. We will see how accurate this prediction was. With over 1 billion monthly active users on Facebook globally, I can’t imagine this changing so dramatically.
Going back to the point about continually investing in all digital areas of your business, we were reminded about how giants can fall with examples cited including Nokia and Blackberry. Continual innovation of your digital assets, products and services is essential to survive.
Discussions soon turned to educational establishments, with a bit of unfair bashing as we are starting to see many leading organisations such as MMU and Salford University running courses designed for the needs of the digital world. That said, there are still many educational establishments who are still running marketing courses that don’t even touch on the digital world, which are totally pointless in this modern day and age we live in.
Google’s recent 5 predictions were highlighted on the day which I’ll expand on a little to put them into context;
- Acceleration of everything: This needs no further explanation. The rate of change for digital technologies shows no sign of slowing
- Ubiquitous internet: Internet is soon going to be available anywhere and everywhere. People expect this. Manchester city centre now offers free WiFi, most bars/cafes/restaurants offer free WiFi. This significantly changes how people behave, to the point that they have access to everything from anywhere. This does raise some serious security related issues which we will cover in more detail in another blog post as it is a serious area businesses need to consider and plan for.
- Any and all screens are a gateway: The idea of a computer has gone. Anything can be a computer these days to the point whereby screens and devices are simply a gateway for you to access anything you need online.
- Everyone is informed: No longer does information or knowledge have to sit in silos. The Government Dashboard is a prime example of the UK Government leading the way in this area.
- Internet of Things: This is going to change the world we live in
The idea around watching YouTube on the TV, Game of Thrones on the PC, playing games on a mobile device and watching iPlayer on a tablet is natural to the younger generations. There are no longer clear boundaries of what activities you perform on different devices. KPMG put together a global report that looks at The Changing Landscape of Disruptive Technologies [PDF] which is well worth a read through the key statistics and findings. Putting this into perspective, a piece of technology launched a few years ago from NEC was brought up. The technology turns traditional billboards into smart billboards whereby content is personalised to you as a person. The billboards can understand your gender, approximate age, facial recognition and more. Personalised advertising using traditional methods. More information can be found here and here. While I’m not too sure this will come to fruition on the masses, it is never the less interesting technology and shows where the future is heading.
Next we looked at open data and the importance of sharing data across towns, cities and countries. Leeds have the fantastic Leeds Data Mill which shares over 140 open data sets within the city. With data sets ranging from locations of parks, fire stations and more, it is a good starting point to a fully open data platform for anyone to access.
All in all, another insightful event discussing lots of topics that businesses of all types need to take advantage of. With endless changes in the digital world, it can be confusing for a lot of businesses to see how these apply to your own situation. We speak with a lot of companies in very similar situations, whereby they are a little confused about where to start. Let’s meet up for a coffee to see how we can help your business.
by Michael Cropper | Mar 24, 2015 | SEO |
We recently migrated over to a UK leading web hosting infrastructure which involved migrating a large number of websites from one web server to another, and we did this with zero downtime. Which meant that the business websites involved never suffered from lost traffic, sales or enquiries. This is not as straight forward as it sounds on the face of things and requires planning and careful implementation to ensure all data, databases, files, settings, configurations and more are transferred with ease. As this is a common problem for people I thought it would be good to document the steps we took which served us well. Depending on the server technology you are moving from and to will depend on how simple (or difficult) this will be for you to implement. To Buy Server, you have to understand these guidelines are generic so you should be able to take what you need from these and see how this fits in with your technology.

DNS Records
Depending on where your DNS records are setup, if you are using your current DNS records, if you are using new DNS records or something else – will fully depend on if this is relevant for you.
If your current name servers are set to your old hosting provider such as ns1.your-web-host.com and ns2.your-web-host.com then this makes life a little simpler for you. When the time is right, you can simply point your domain names at the new web server by changing the name servers to ns1.your-new-web-host.com and ns2.your-new-web-host.com. That said, many people prefer branded name servers, such as the ones we run for ns3.contradodigital.com and ns4.contradodigital.com. This causes a few more challenges when migrating branded name servers.
If you are wanting to migrate branded name servers then you need to set up an interim stage. For us, our old branded name servers were set up as ns1.contradodigital.com and ns2.contradodigital.com which pointed to the old DNS server (a specific IP address) which then handled the traffic to websites with these name servers and pointed this traffic to the correct web server. If we were to simply migrate the DNS server IP address for ns1.contradodigital.com and ns2.contradodigital.com over to the new DNS server, this would take time to propagate, up to 48 hours which could cause inconsistent behaviour for users accessing websites listed.
Instead, by setting up new name servers which point to the new DNS server we can have ns3.contradodigital.com and ns4.contradodigital.com which can then propagate throughout the Domain Name System until we are ready to officially migrate the websites over. Once we are confident that the new name servers have propagated (see http://dnswatch.info to check) we can then begin the migration.
Beyond this, if you have any A, TXT, MX records or other that are configured on your old server, then make sure these are migrated too.
Transfer Data
Getting all of your data, files, databases, settings and more from your old web server over to your new website can be a challenge. Thankfully for us, we use a leading web server management system, cPanel which comes with a handy little transfer tool. This allows the old and new servers to talk to each other and automatically migrate everything over. This setup does require that you have SSH Root access to both servers, which you may or may not have depending on the old technology you are using.
If you are migrating between different web server control panels then this is going to be a much more manual process and often requires a detailed checklist to make sure you have transferred everything correctly and it has been implemented correctly on your new system.
It is important to reiterate this, but make sure you have transferred absolutely everything on your web server. To give you an idea this could include; files, redirects, email forwarders, distribution groups, emails, databases, FTP accounts, user logins, server logs (if needed) and more. Depending on how much of the functionality you use on your old and new webserver will depend on the areas that you need to check over. Always by over cautious to make sure you have checked everything since if you miss anything then you are unlikely to be able to recover this once you have cancelled the subscription on your old web server.
Website Migration
Once you have successfully migrated all of your data, it’s time to start migrating your websites to run from the new server and get rid of the old server. To start things off, start with a non-descript website if possible to make sure that the process has worked for your individual settings. The details above are specific to what we did and may or may not work for you. The final step is to switch your name servers so your domain names will be looking at your new web server instead of your old one.
Once you have updated the name servers for the test domain, then you can check that everything is working correctly before migrating the remaining domains on the system. This process will allow you to migrate your web servers seamlessly with zero downtime. This is a little more challenging for large scale ecommerce websites due to data continuity related to transactional data, but this is a little outside the scope of this blog post as this again depends on the technology being used related to the ecommerce setup.
Nuances
A few other points to note about web server migration is that you can trip up if you are migrating to servers with different versions of software running (PHP for example), different file systems, different operating systems, different access rights and more. When upgrading your web server, you are likely moving away from technology that isn’t suitable for your needs anymore or is limiting in some way. This causes a few problems naturally which may need to be overcome. You may also have some specific technology, non-standard and inaccessible server settings configured on your old server which can easily be missed during the migration. To avoid tripping up on some of these issues, it is always recommended to speak with your current web host to understand the full technical setup and software that is installed to make sure you have everything installed on the new server that is needed to support the websites and web applications that you are running.
Summary
The information outlined worked for us. It may not work for you. Understand the technology you are working with, in terms of what you are moving from and what you are moving to. If you are in any doubt, get in touch and we can help you with this process. Working with industry leading web hosting solutions means that we have a lot of experience working with great solutions, and also very poor solutions that people are migrating away from.

![]()









































