Another day, another hacked website. This time, thankfully due to the security and backup solutions in place, restoring this backup was relatively straight forward and much cheaper than if these security solutions and automated backups weren’t in place.
Usually we get businesses running to us when things have gone wrong and they have failed to plan accordingly for when this happens. Thankfully, whichever way you look at this, this business had been hacked before and since then had additional levels of security and automatic backup solutions in place to reduce the risk and help to resolve issues when they do go wrong. This being said, on this occasion, no amount of technology can protect against basic human error and weak passwords.
Below is a brief outline about what happened. It’s only a rough guide but does go to show how something as simple as a weak password can even bypass the additional security. And most importantly, this highlights the reason why you should always be planning for the worst and expecting the best. Naturally, all of the sensitive information is blocked out of the screenshots, as is information about the hackers as they deserve no additional praise for the work they have done.
Website takeover

Server Logs
The website isn’t hosted with ourselves, so by the time we investigated this we couldn’t access the server logs as web server had already been rebooted, so the error logs lost.
WordPress Access Logs
Show that the user ‘Admin’ logged in on 08-05-2016 at 8:55 am;
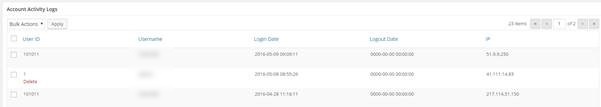
From the IP address 41.111.14.83 which is based in Algeria, Africa;
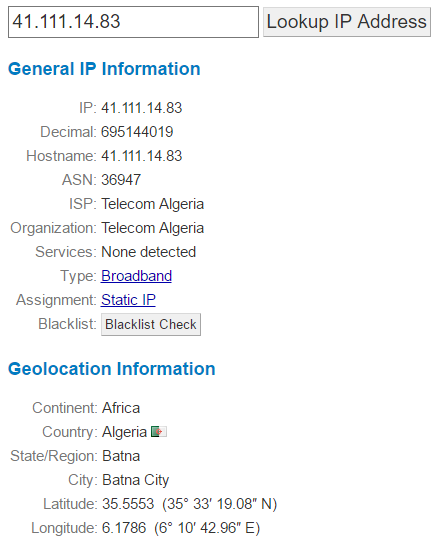
This username belonged to a member of staff at the web hosting company whose account was compromised and used to initiate the attack;
![]()
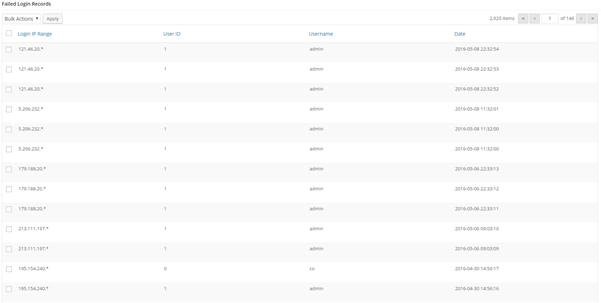
Which when looking at the access logs on the date, there weren’t many failed login attempts which suggests that their password was rather weak;
Plugin Uploaded
Now the hackers had Administrator access to the site, they uploaded a plugin which allowed them to upload a script to the site and run this script via the command line;
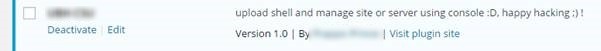
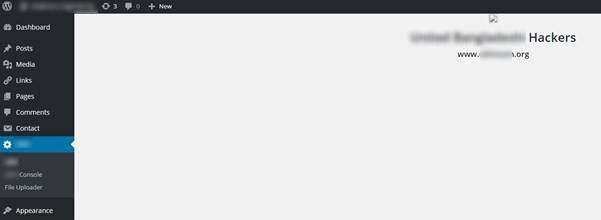
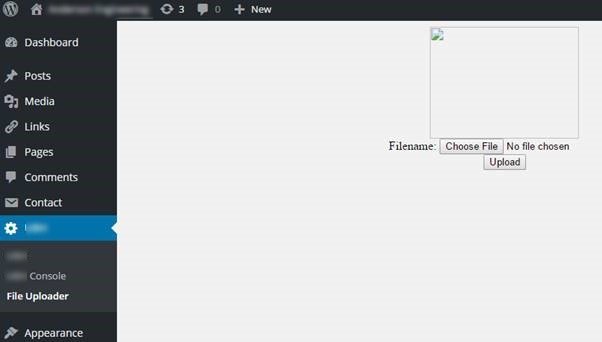
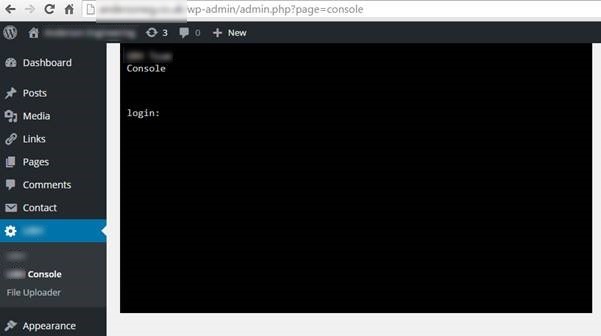
This plugin & script allowed the hackers to take over control of the whole site and display the messages.
Summary
While this does seem like an extremely simple thing, essentially guessing someone’s password. This does highlight the importance of being able to trace exactly what happened when a hack occurs. Being able to track the path the hackers took to exploit the website ultimately led to the root cause of the problem being able to be fixed to prevent this from happening again.
If you don’t have website security and automated backups in place, then get in touch. Seriously, get in place what you need to before you get hacked. Do not think that this will not happen to you. As we have just shown, even with added levels of security in place, a hack can be as simple as a weak password. Make sure you have the right technology in place to be able to identify the root causes of problems when they do occur to save yourself significant time and money dealing with things when the inevitable does happen. No-one wants to get hacked and everyone believes they will never be a target. The reality is that most businesses will get hacked at least once in their lifetime. It is only the large businesses that we often hear about in the news. In this instance, this is a story of a small business, less than 10 staff, for whom this kind of issue is something that they would prefer not to have to deal with.
In this example, we were able to respond to the issue, identify the affected areas of the website, identify the root cause & patch all within a morning. All for the cost of the price of a coffee per day. You have to ask yourself, if you don’t have the right technologies in place to deal with situations like this, how long would your website have been offline for? A day or two? A week? More? I can’t stress enough that preparation is key when dealing with cybercrime. Your digital back door is probably wide open, waiting for someone to walk by and exploit it, you just probably aren’t aware as it’s not something you can physically touch and feel.
Michael Cropper
Latest posts by Michael Cropper (see all)
- WGET for Windows - April 10, 2025
- How to Setup Your Local Development Environment for Java Using Apache NetBeans and Apache Tomcat - December 1, 2023
- MySQL Recursive Queries – MySQL While Loops – Fill Zero Sum Dates Between Dates - October 6, 2023
