Cyber Security Resources
Growing list of cyber security related material to keep your website and digital assets safeCyber security is a growing issue for all businesses who operate online yet there is an enormous gap in education when it comes to how businesses and website owners need to protect their self. It is far too easy for businesses to take a lax approach to cyber security which often results in disastrous consequences from websites going offline for a long period of time as a minimum, to brand reputational damage and even as far as exposing all customers personal details and data.
Planning and preparation is key to minimise the risks for your business and digital assets. This list of resources is designed to be a signposting page to all of the great resources available which covers the important topics related to cyber security that you need to be aware of and check your systems for vulnerabilities before cyber criminals do.
The resources start at the basics and do go quite technical which we make no apologies for. If you don’t personally understand some of the topics in the resources listed, then get in touch and we can talk you through things in more detail and test your systems accordingly for issues.
The Risks
Before we jump into the resources, ask yourself a few questions about your digital assets to put cyber security into context;
- When a cyber security issue happens, how quickly can you get your website back up and running?
- How much will this website down-time cost your business in terms of revenue lost through missed sales?
- What data do you store about customers on your website and how is this protected?
- What is the schedule for your automated website backup solution?
- How is your web server configured and is your website at risk by being on a shared platform?
- Are you running the latest CMS version, the latest PHP version, the latest MySQL version and other technology on your server, or do you not know when the last time this was updated?
Based on experience, we know that most businesses are at risk in one way, shape or form. To put this into perspective, below are a few WordPress statistics for self-hosted WordPress installations taken from the WordPress Statistics data;
WordPress Versions
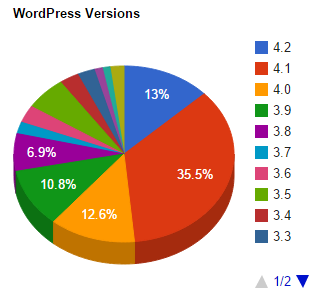
WordPress 4.1 was released to patch a critical security update, yet at the time of writing weeks after this update, over 50% of WordPress websites are still running older versions that are vulnerable to attacks. Bearing in mind that WordPress powers over 23% of websites on the internet, this is a lot of websites that are vulnerable.
PHP Versions
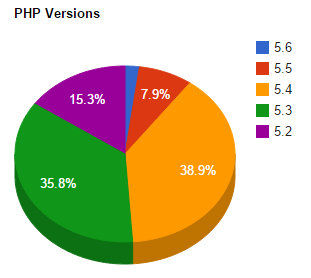
PHP is the language that WordPress is built on. Just as all technology, there are different versions that are installed on web servers around the world. And just as with all technology, older versions are often vulnerable to attacks when people know how to exploit things. To put this into perspective, websites such as CVE Details lists known exploits for anyone to browse through which is essentially a shopping list for cyber criminals. For example, here are known vulnerabilities related to PHP Version 5.5. Maybe it is worth upgrading to the latest version?
MySQL Versions
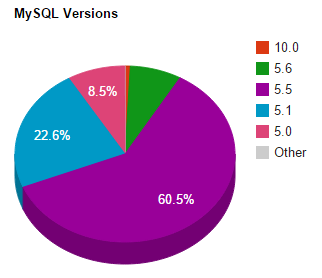
Following a similar trend above, there are over 135 MySQL 5.5 vulnerabilities. Yet over 60% of WordPress websites are running on web servers that are running on version 5.5. Maybe time for an upgrade?
Other Technology
The above examples have been given for WordPress specifically due to the popularity of the platform. The same issues lie in all technologies which is why cyber security is hugely important to keep up to date with vulnerabilities and protect your website.
We naturally keep up to date with this and as one of our services work to keep your WordPress website safe and secure. Keeping up to date with the latest cyber security news is a big job but is an essential one to mitigate risks to your business which is why we take cyber security seriously.
The examples given above aren’t a hard and fast rule that you must always be running the latest version since your application or systems may not be at risk depending on their functionality. Likewise, there are many sub-versions within the headings above which have patched known vulnerabilities already. Hopefully this gives a bit of context to cyber security risks though and the importance of taking this seriously.
The Basics on Cyber Security
Ok, so let’s start with the basic resources.
Cyber Streetwise

Resource: https://www.cyberstreetwise.com/
Resource from central government which covers a wide range of topics including;
- Secure your devices online: Firewalls; Passwords; Security Software; Software Updates; Wireless Networks; Internet of Things; Common Scams
- Protect your online privacy: Internet safety for children; Online dating; Passwords; Social networking; Common scams
- Look after your money online: Banking online securely; Safe shopping online; Common scams
- Defend your business: IT policies; Office IT; Selling online; Common scams; Managing staff privileges; Understanding the Data Protection Act; Bring Your Own Device (BYOD)
Cyber Security Guidance for Business
![]()
Resource: https://www.gov.uk/government/publications/cyber-risk-management-a-board-level-responsibility
Resource from central government which covers a wide range of topics including;
10 Steps to Cyber Security
- User education and awareness – Read more
- Home and mobile working – Read more
- Secure configuration – Read more
- Removable media controls – Read more
- Managing user privileges – Read more
- Incident management – Read more
- Monitoring – Read more
- Malware protection – Read more
- Network security – Read more
- Information risk management regime – Read more
Summary document Reducing the Cyber Risk in 10 Critical Areas [PDF]
10 steps A Board Level Responsibility
Protection of key information assets is critical
- How confident are we that our company’s most important information is being properly managed and is safe from cyber threats?
- Are we clear that the Board are likely to be key targets?
- Do we have a full and accurate picture of:
- the impact on our company’s reputation, share price or existence if sensitive internal or customer information held by the company were to be lost or stolen?
- the impact on the business if our online services were disrupted for a short or sustained period?
Exploring who might compromise our information and why
- Do we receive regular intelligence from the Chief Information Officer/Head of Security on who may be targeting our company, their methods and their motivations?
- Do we encourage our technical staff to enter into information-sharing exchanges with other companies in our sector and/or across the economy in order to benchmark, learn from others and help identify emerging threats?
Pro-active management of the cyber risk at Board level is critical
- The cyber security risk impacts share value, mergers, pricing, reputation, culture, staff, information, process control, brand, technology, and finance. Are we confident that:
- we have identified our key information assets and thoroughly assessed their vulnerability to attack?
- responsibility for the cyber risk has been allocated appropriately? Is it on the risk register?
- we have a written information security policy in place, which is championed by us and supported through regular staff training? Are we confident the entire workforce understands and follows it?
10 Steps The Executive Companion
- Do you have the right skills to effectively manage your cyber risk?
- What information should you protect?
- What players might pose a risk to your information?
- What are the risks to your information and how much risk can you accept?
- What measures do you need?
- Do the security measures work?
- What would happen to the business if one of your risks became a reality?
- How do you embed risk management within your company?
- How can you ensure that you have the best possible understanding of the threat to your business?
- Cyber Essentials
Common Cyber Attacks – Reducing the Impact
Resource: Common Cyber Attacks – Reducing the Impact [PDF]
- Who might by attacking you? Cyber criminals; Industrial competitors; Foreign intelligence services; Hackers; Hacktivists; Employees
- Untargeted attacks: Phishing; Water holing; Ransomware; Scanning
- Targeted attacks: Spear-phishing; Deploying a botnet; Subverting the supply chain
- Understanding vulnerabilities: Flaws; Features; User error;
- Reducing your exposure: Firewalls and internet gateways; Network perimeter defences; Web proxy; Web filtering; Content checking; Firewall policies; Malware protection; Patch management; Whitelisting and execution control; Secure configuration; Password policy; User access control
UK Cyber Security Strategy
Resources: https://www.gov.uk/government/policies/keeping-the-uk-safe-in-cyberspace
Outlining a lot of the work central government are currently doing to advice businesses around cyber security related matters including;
- Cyber Essentials Scheme
- Small Businesses: What you need to know about Cyber Security [PDF]
- Cyber Security – The UK’s approach to exports [PDF]
Information and Data Protection for Cyber Security
Information Commissioners Office
Data protection guidelines for small businesses;
- Getting it right: a brief guide to data protection for small businesses [PDF]
- Getting it right: small business checklist [PDF]
- Personal information online: small business checklist [PDF]
- A practical guide to IT security: ideal for the small business [PDF]
- Training checklist for small and medium-sized organisations [PDF]
- Outsourcing – a guide for small and medium-sized businesses [PDF]
- Collecting information about your customers: small business checklist [PDF]
- Direct marketing guidance [PDF]
- Buying and selling customer databases [PDF]
- Register under the Data Protection Act – For companies who process personal information and are required to register. User the self-assessment tool to find out if you need to register.
- The Guide to Data Protection [PDF]
- Training guides to promote data protection within your organisation
- The Guide to Privacy and Electronic Communications [PDF]
Further guidance for small businesses – Read more
Further guidance for organisations – Read more
ICO Guidance for Technology;
8 Principles of Data Protection;
- Fair and lawful
- Purposes
- Adequacy
- Accuracy
- Retention
- Rights
- Security
- International
Read full guidelines to data protection
CREST Resources
CREST is a not for profit organisation that serves the needs of a technical information security marketplace that requires the services of a regulated professional services industry. They provide guidelines for industry experts, businesses and more;
- CREST Implementation Guide [PDF]
- A Guide to the Cyber Essentials Scheme [PDF]
- Penetration Testing Services Procurement Guide [PDF]
- Procuring Penetration Testing Services [PDF]
- Cyber Security Incident Response Guide [PDF]
- Cyber Security Incident Response Guide Supplier Selection Guide [PDF]
Cyber Security Incident
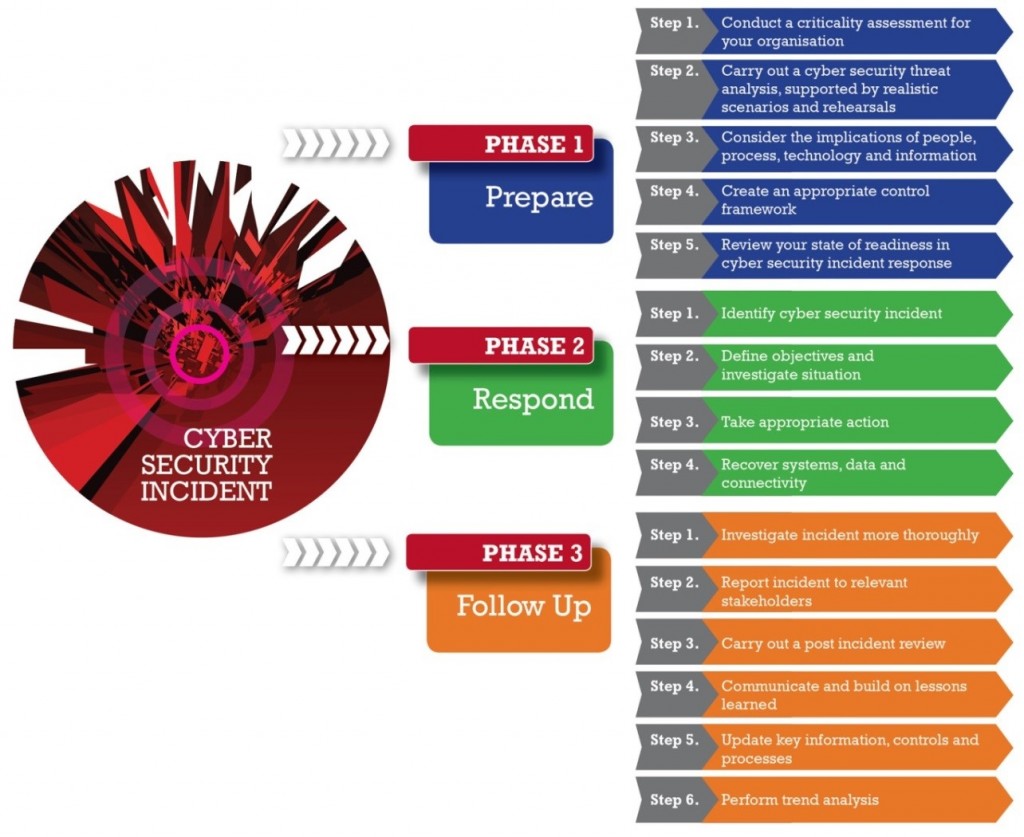
Source: http://www.crest-approved.org/wp-content/uploads/15-step-response-process.jpg
The above guides from CREST are just a small amount of the resources that are available throughout their website. Take a good look around.
Technical Cyber Security Topics
Now onto some of the more technical aspects related to cyber security and most importantly how to protect against these known and common vulnerabilities.
OWASP Top 10
Resource: OWASP Top 10 2013 (Latest Version) [PDF]
Listing the top most critical web application security risks. The Open Web Application Security Project (OWASP) is an open community dedicated to enabling organisations to develop, purchase and maintain applications that can be trusted.
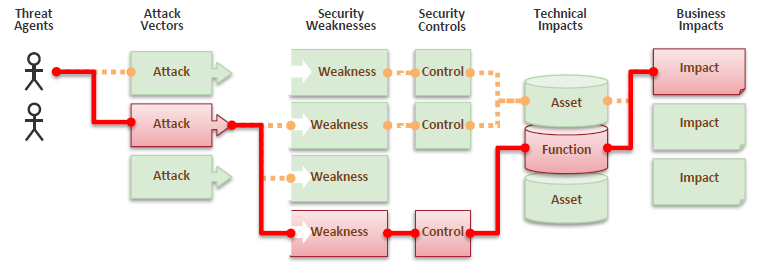
A1 – Injection
Injection flaws, such as SQL, OS and LDAP injection occur when untrusted data is sent to an interpreter as part of a command or query. The attacker’s hostile data can trick the interpreter into executing unintended commands or accessing data without proper authorisation
A2 – Broken Authentication and Session Management
Application functions related to authentication and session management are often not implemented correctly, allowing attackers to compromise passwords, keys, or session tokens, or to exploit other implementation flaws to assume other users’ identities
A3 – Cross-Site Scripting (XSS)
XSS flaws occur whenever an application takes untrusted data and sends it to a web browser without proper validation or escaping. XSS allows attackers to execute scripts in the victim’s browser which can hijack user sessions, deface websites, or redirect the user to malicious sites
A4 – Insecure Direct Object References
A direct object reference occurs when a developer exposes a reference to an internal implementation object, such as a file, directory, or database key. Without an access control check or other protection, attackers can manipulate these references to access unauthorised data.
A5 – Security Misconfiguration
Good security requires having a secure configuration defined and deployed for the application, frameworks, application server, web server, database server and platform. Secure settings should be defined, implemented, and maintained, as defaults are often insecure. Additionally, software should be kept up to date.
A6 – Sensitive Data Exposure
Many web applications do not properly protect sensitive data, such as credit cards, tax IDs, and authentication credentials. Attackers may steal or modify such weakly protected data to conduct credit card fraud, identity theft, or other crimes. Sensitive data deserves extra protection such as encryption at rest or in transit, as well as special precautions when exchanged with the browser.
A7 – Missing Function Level Access Control
Most web applications verify function level access rights before making that functionality visible in the UI. However, applications need to perform the same access control checks on the server when each function is accessed. If requests are not verified, attackers will be able to forge requests in order to access functionality without proper authorisation.
A8 – Cross-Site Request Forgery (CSRF)
A CSRF attack forces a logged-on victim’s browser to send a forged HTTP request, including the victim’s session cookie and any other automatically included authentication information, to a vulnerable web application. This allows the attacker to force the victim’s browser to generate requests the vulnerable application thinks are legitimate requests from the victim.
A9 – Using Known Vulnerable Components
Components, such as libraries, frameworks, and other software modules, almost always run with full privileges. If a vulnerable component is exploited, such an attack can facilitate serious data loss or server takeover. Applications using components with known vulnerabilities may undermine application defences and enable a range of possible attacks and impacts.
A10 – Unvalidated Redirects and Forwards
Web applications frequently redirect and forward users to other pages and websites, and use untrusted data to determine the destination pages. Without proper validation, attackers can redirect victims to phishing or malware sites, or use forwards to access unauthorised pages.
Summary
Within the OWASP Top 10 document is information to check how vulnerable your web application is to the specific threat along with how to prevent and protect yourself from known vulnerabilities.
Next steps for developers include;
- Application security requirements
- Application security architecture
- Standard security controls
- Secure development lifecycle
- Application security education
Read the full OWASP Dev Guide on GitHub for detailed recommendations
Java Development Secure Coding Guidelines
Following on from the OWASP guidelines, more specific guidelines for Java development can be found at;
There are an awful lot of security topics related to every programming language, a little too much to list every single one here.
Final Resources
A few other resources that haven’t been mentioned above which are an interesting read for those wanting to dig a little deeper in the field of cyber security;
- UK National Security Strategy: https://www.gov.uk/government/uploads/system/uploads/attachment_data/file/61936/national-security-strategy.pdf
- UK Cyber Security Strategy: https://www.gov.uk/government/uploads/system/uploads/attachment_data/file/60961/uk-cyber-security-strategy-final.pdf
- HMG Security Policy Framework: https://www.gov.uk/government/uploads/system/uploads/attachment_data/file/316182/Security_Policy_Framework_-_web_-_April_2014.pdf
- Introduction to Cyber Security course from the Open University: http://www.open.edu/openlearn/futurelearn/cyber-security
- Competitive analysis of the UK cyber security sector: https://www.gov.uk/government/uploads/system/uploads/attachment_data/file/259500/bis-13-1231-competitive-analysis-of-the-uk-cyber-security-sector.pdf
- Information Security Breaches Survey 2014: http://www.pwc.co.uk/assets/pdf/cyber-security-2014-technical-report.pdf
- Metropolitan Police Fraud Alert: http://content.met.police.uk/Site/fraudalert
- MetaPack for high end ecommerce websites: http://www.metapack.com/
Summary
There are an awful lot of resources throughout this document all of which are related to cyber security. Whether this is educational and awareness type content or more technical hands-on content for those implementing the changes, there is something for everyone. The actual hands on work behind all of these resources is an enormous topic and is far too big to cover within this Cyber Security Resource.
If any of the topics raised throughout this document worry you, then get in touch to discuss how our expertise can be used to put your mind at ease. Working with these technologies daily we have a good background and experience working with many systems, processes, training and more related to websites, technologies and security which integrates through everything. Get in touch to discuss your specific needs.
